Ethereum Classic Attack, 8 August: Catch me if you can
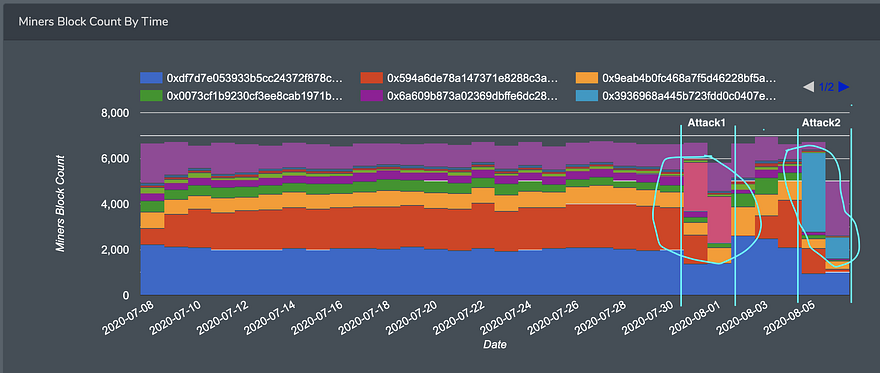
After attacking the Ethereum classic chain on July 31, 2020, the same Attacker attacked the ETC chain again yesterday. The massive reorganization of 4236 blocks happened in Ethereum Classic blockchain at 2020–08–06 02:54:27 UTC.
It affected blocks from 10935623 to 10939858. Attacker mined the first block at 2020–08–05 11:50:20 UTC, so this attack lasted 15 hours and 6 minutes.
Key Takeaway
This time attacker was trying to double-spend 465,444 ETC(approx $3.3 M). Based on our investigation, the attacker successfully double-spent 238,306 ETC ($1.68 M) through Bitfinex and another crypto service. In addition, the attacker also got 14.2K ETC as a block reward, which we are not included in our double-spent calculation.
Hash Power
The attacker probably used the same mining source, Nicehash daggerhashimoto, as observed on the following graph.
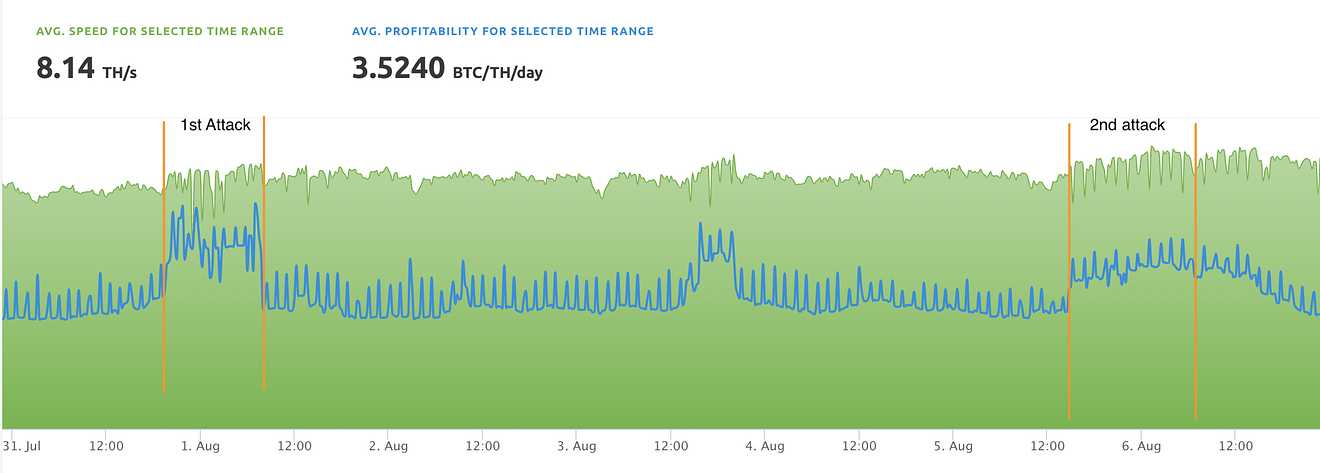
nicehash showing the price and TH/sec in UTC+3 timezone
Attacker, 0x3936968a445b723fdd0c0407efffcaecb07cab19 mined 4236 blocks consecutively, plus some extra blocks after the re-org. The block reward from this attack was, 14,234.30 ETC, which still resides on the attacker’s wallet.
The attack is clearly visible on the miner distribution chart on Bitquery.
Double-Spent
Our analysis shows, it was the same Attacker, using exactly the scheme as we described in our recent investigation of the attack on July 31st.
This time Attacker included seven transfers in the mined blocks. The total amount of these transactions was 465,444 ETC (approx $3.3 M).
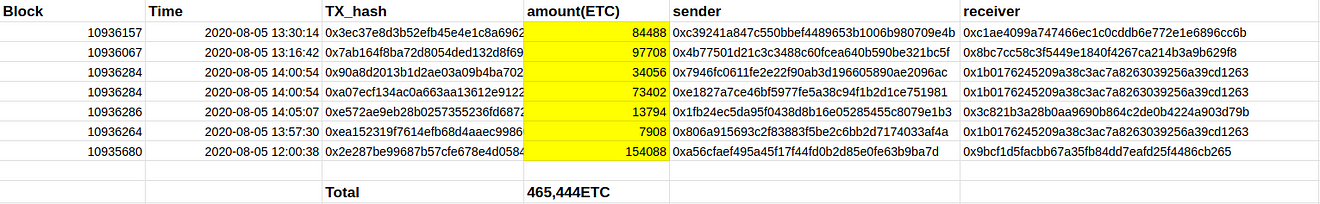
Where the money comes from?
This time the attacker used the money from the first attack, July 31. In our last analysis, we showed how the attacker double spent the money by sending it to Exchange and also his/her own wallet. This time, the attacker used the ETC left from the first attack.
For example the address 0x305292887ad1ffa867e8564c804575f3d7a19a1f is the source of money for the first transaction in the list. This address was used in the first attack. Similarly, other addresses mentioned in the above transaction list also got money from the first attack.
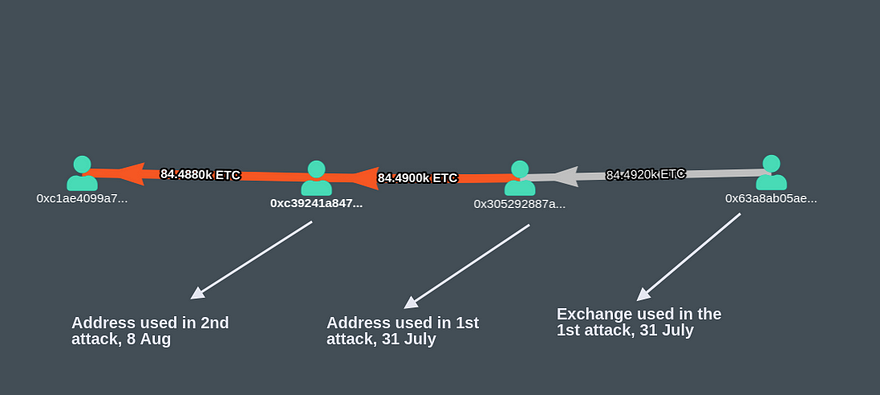
0xc39241a847c550bbef4489653b1006b980709e4b
Where the Attacker double-spent this time?
The blocks mined by the attacker included transactions in which the attacker sent his/her money to different wallets controlled by him/her. This activity was not visible to anyone as the attacker did not publish any transactions or the blocks, similar to the last attack.
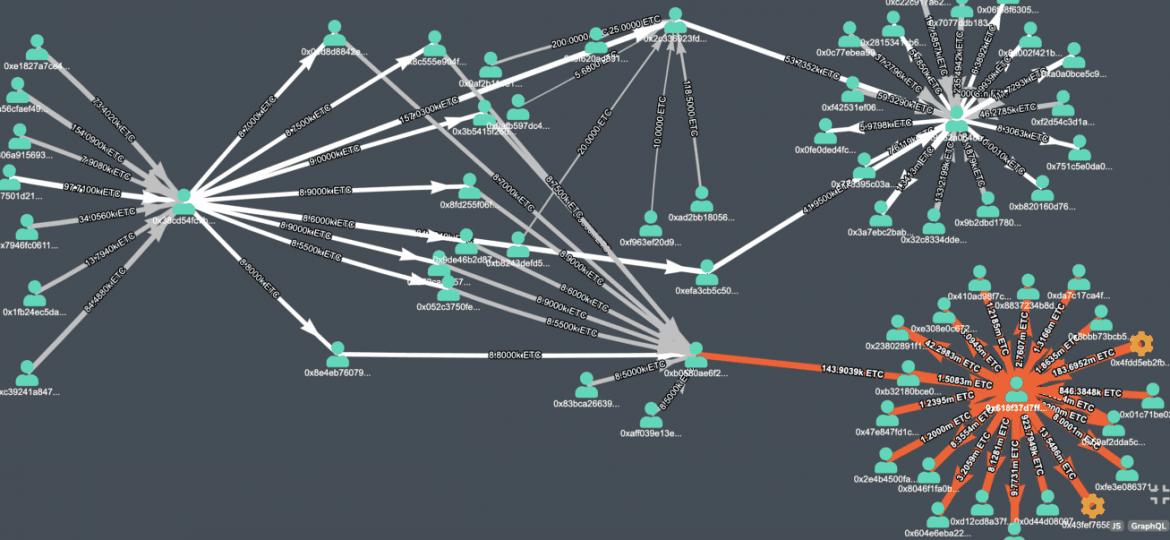
On the other hand, the chain which was visible to everyone (now reorged and discarded), the attacker first collected the money on the address 0x38cd54fc7b1fe7994355fce1d75c9c4bd7335a46. After that, the attacker distributed money to different addresses.
All these transactions happened during the time of the attack when the attacker silently mined the forked blocks.
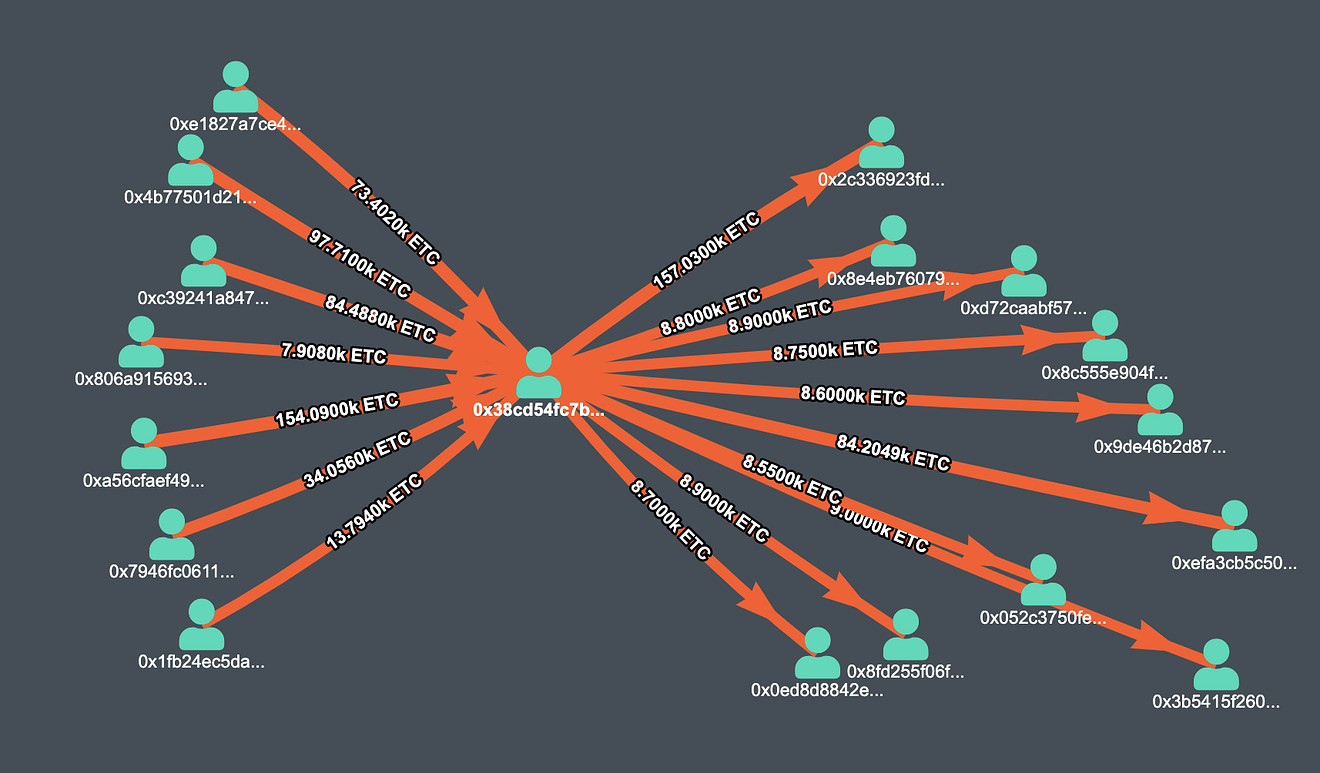
Money distributed to multiple addresses from 0x38cd54fc7b1fe7994355fce1d75c9c4bd7335a46
Apparently, the final target was some exchanges and other crypto services, and we can find some of them in the following image.
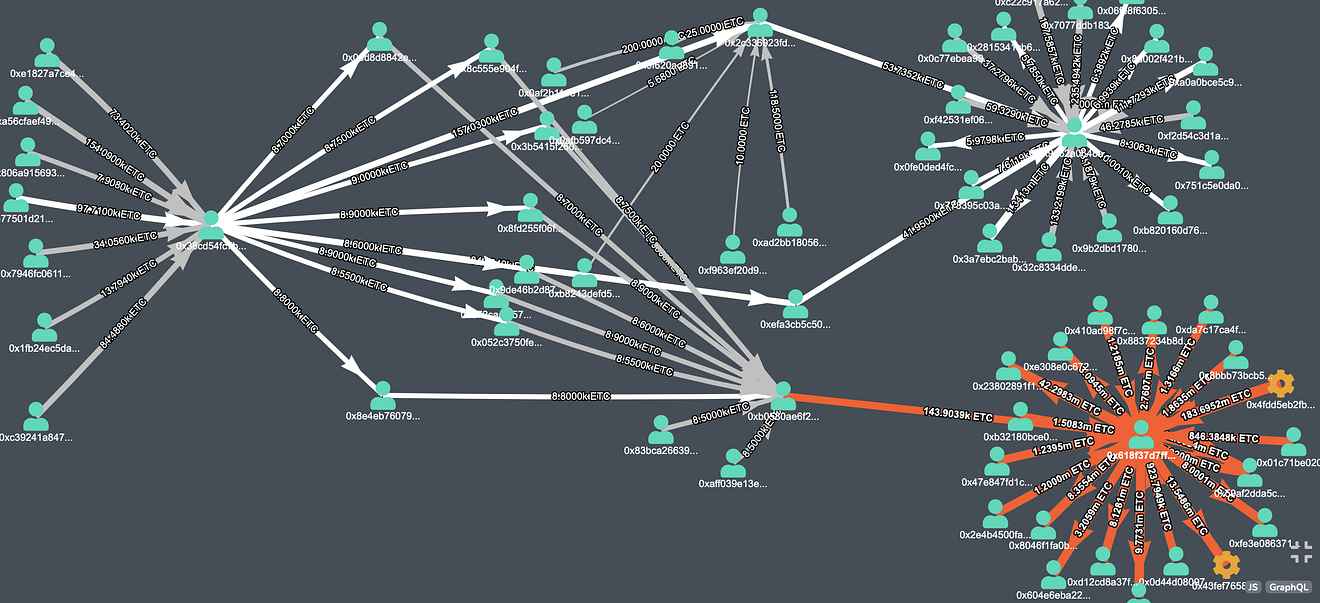
Money originated from 0x38cd54fc7b1fe7994355fce1d75c9c4bd7335a46, end up on exchanges
The “fireworks” on the right side of the graph are Exchanges, where Attacker sent the money. The attacker must have converted those ETC into fiat or other cryptocurrencies.
The following address which received money from the attacker belongs to Exchanges and other crypto services.
- 0x618f37d7ff7b140e604172466cd42d1ec35e0544, which we believe, belongs to Bitfinex exchange based on this post, received 143,000 ETC in several transactions. You can find the complete transaction details here.
- 0x9662a0648aa48592a63509c092ab05adf0a84cc9 received 95,650 ETC in multiple transactions. We were not able to identify the crypto service which owns this address. The two biggest transactions, which was received by this address are mentioned below.
- 41,950 ETC in transaction
- 53356 ETC in transaction
Total money loss
Our investigation shows that Bitfinex lost 143K ETC (~$1M) and we were not able to identify the other service mention above who lost 95K ETC (~680K). In total, we were able to able to verify that the attacker profited $1.68M (At least) from this attack.
The mentioned crypto service can identify the attacker based on the above transactions.
Wrapping up…
We believe the double-spent this time would have been caught. Our transaction monitoring technology, Coinpath®, built to trace blockchain money flow and would have flagged these transactions for further investigation. If you are looking for blockchain transaction monitoring technology, get in touch with us sales@bitquery.io.
Note: Special thanks to Yaz Khoury for reviewing the article.
About Coinpath®
Coinpath® APIs provide blockchain money flow analysis for more than 24 blockchains. With Coinpath’s APIs, you can monitor blockchain transactions, investigate crypto crimes such as bitcoin money laundering, and create crypto forensics tools.
If you have any questions about Coinpath®, ask them on our Telegram channel or email us at sales@bitquery.io. Also, subscribe to our newsletter below, we will keep you updated with the latest in the cryptocurrency world.
Coinpath® is a Bitquery product. Bitquery is a set of tools that parse, index, access, search, and use information across blockchain networks in a unified way.
About Bitquery
Bitquery is a set of software tools that parse, index, access, search, and use information across blockchain networks in a unified way. Our products are:
-
Coinpath® APIs provide blockchain money flow analysis for more than 24 blockchains. With Coinpath’s APIs, you can monitor blockchain transactions, investigate crypto crimes such as bitcoin money laundering, and create crypto forensics tools. Read this to get started with Coinpath®.
-
Digital Assets API provides index information related to all major cryptocurrencies, coins, and tokens.
-
DEX API provides real-time deposits and transactions, trades, and other related data on different DEX protocols like Uniswap, Kyber Network, Airswap, Matching Network, etc.
If you have any questions about our products, ask them on our Telegram channel or email us at sales@bitquery.io. Also, subscribe to our newsletter below, we will keep you updated with the latest in the cryptocurrency world.
Also Read
- Ethereum Classic 51% Chain Attack July 31, 2020
- Attacker Stole 807K ETC in Ethereum Classic 51% Attack
- Coinpath® – Blockchain Money Flow APIs
- avast premier license file 2018
- Cryptocurrency Money Laundering Explained
- How Upbit hackers laundered millions using crypto exchanges?
- Twitter Hack — Track Bitcoin crimes in real-time using Coinpath®
Subscribe to our newsletter
Subscribe and never miss any updates related to our APIs, new developments & latest news etc. Our newsletter is sent once a week on Monday.