
Unveiling the Power of Blockchain: Tracking Bitcoin Seized by the US Government
In the ever-evolving landscape of financial transactions, the advent of blockchain technology has ushered in a new era of transparency and accountability. Bitcoin, the pioneer of cryptocurrencies, is no stranger to legal scrutiny, often finding itself at the center of investigations and law enforcement actions. One intriguing aspect of this intersection between technology and regulation is the use of blockchain data to track and manage Bitcoin seized by the US government.
From the groundbreaking Silk Road seizure to the notorious Bitfinex hack, and the recent high-profile case involving James Zhong, instances of Bitcoin confiscation by the US government have not only grabbed headlines but also prompted a closer examination of the role blockchain data plays in these legal proceedings.
Evolution of Cryptocurrency Seizures: From Silk Road to Bitfinex Hack and Beyond
The landscape of cryptocurrency seizures is marked by notable events that have shaped both the legal narrative and the evolving technology underpinning digital currencies. The infamous Silk Road case brought to light the intersection of dark web activities and the seizure of Bitcoin as a means of disrupting illegal transactions.
Subsequently, the Bitfinex hack underscored the vulnerability of cryptocurrency exchanges, leading to a significant seizure to mitigate losses. The recent case involving James Zhong adds a layer of complexity, emphasizing the need for advanced tools to navigate the intricate paths of blockchain transactions. In this context, the utilization of data-backed insights, facilitated by Bitquery APIs, emerges as a crucial element in the pursuit of justice and the effective management of seized assets.
Analyzing the US Government's Bitcoin Holdings and Tracking Seized Tokens: A Closer Look at Major Crypto Seizures
As of today,the US government is among the largest Bitcoin holders with over $5B in BTC (estimated; the actual holdings could be much larger) owing to the three major seizures mentioned above. The question that remains unanswered is where is the seized token currently? Is it present at 1 wallet, was it moved across exchanges gradually? Let’s use data to answer these questions. Before we delve into the details, let’s do a quick roundup of some of the biggest seizures of all time.
Between 2011 and 2013, Silk Road was the first major crypto-powered darknet market, Ross Ulbricht, the mastermind behind the Silk Road, faced arrest in 2013. However, the capture of James Zhong, the individual responsible for pilfering 50,000 Bitcoin from the notorious darknet market in 2012, did not occur until November 2021. Zhong pulled off the theft by exploiting a flaw in Silk Road’s Bitcoin withdrawal mechanism for vendors.
In our ongoing exploration of the US government's Bitcoin holdings and the intricacies surrounding major seizures, a pivotal moment occurred on March 7, 2023. The government executed a transfer of 9,000 BTC from the address (bc1qa5wkgaew2dkv56kfvj49j0av5nml45x9ek9hz6), strategically dividing the sum between Coinbase(0.1 BTC) and another address (bc1qe7nk2nlnjewghgw4sgm0r89zkjzsurda7z4rdg) (transferred 8999.9 BTC). This transaction prompts a closer examination of blockchain data, leading us to delve into the web of transactions associated with the Silk Road seizure.
After looking at all the transactions pertaining to the wallet in question during the Silk road seizure, there were few observations
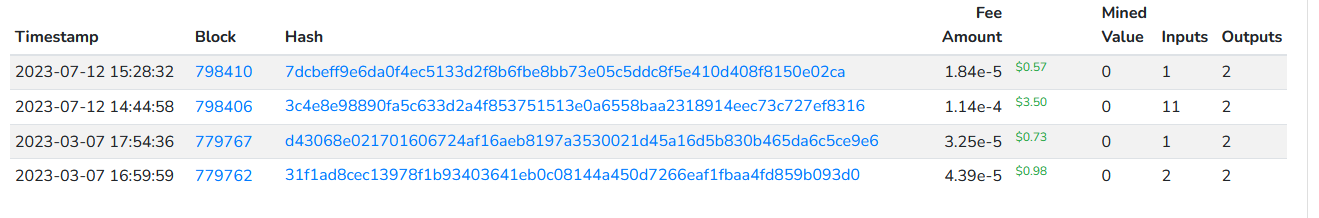
After looking at the individual transactions and looking at the token flow, we found a transactions with a huge outflow
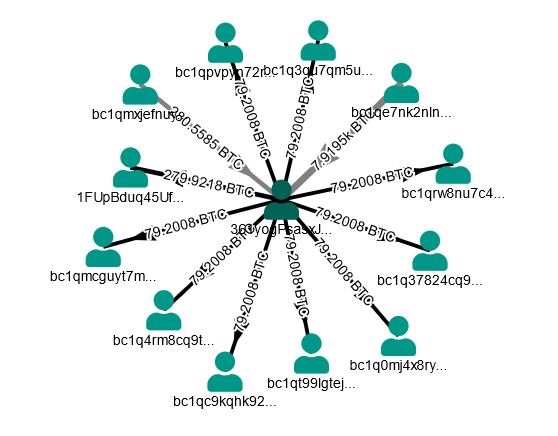
We consider this address as a change address in transaction 31f1ad8cec13978f1b93403641eb0c08144a450d7266eaf1fbaa4fd859b093d0.
From this address, there are 3 main transactions to 3 different accounts:
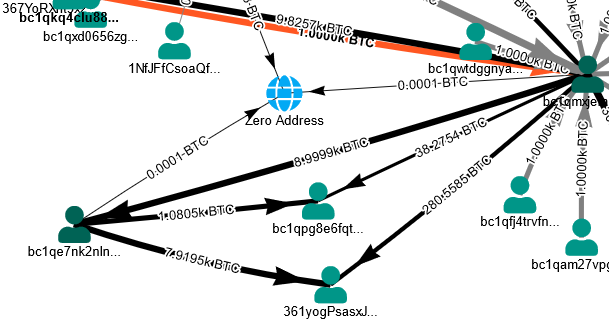
On July 12th, 2023: there was incoming transaction from the account bc1qmxjefnuy06v345v6vhwpwt05dztztmx4g3y7wp which was under scrutiny during the James Zhong case. On March 31 2023, Court documents filed signaled that the US Government plans to sell ~41k BTC related to the James Zhong case in four tranches through 2023.
The 8.999k BTC was then sent to 2 different accounts (361yogPsasxJz6JAaFskmWZes14Gs38ikj) and (bc1qpg8e6fqt53lga68qnyxfnfh6gzc0d88d6mjmu7)
The tokens from 361yogPsasxJz6JAaFskmWZes14Gs38ikj were next sent to 10 different accounts with each receiving 79.2 BTC each
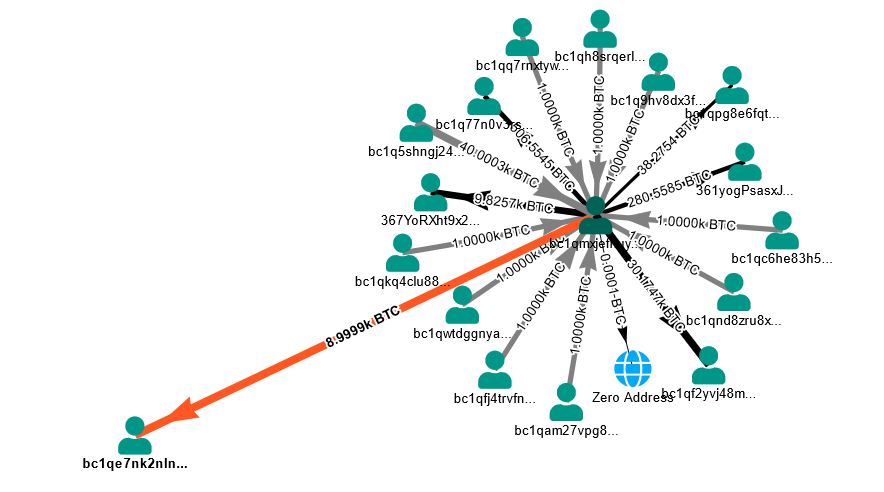
Source; Money flow movement from 361yogPsasxJz6JAaFskmWZes14Gs38ikj via bitquery explorer
On July 12th the Government moved 9,319 BTC, sending 8,200 to a third-party address (361yogPsasxJz6JAaFskmWZes14Gs38ikj). These coins eventually hit exchanges. 1,119 BTC were sent to address bc1qpg8e6fqt53lga68qnyxfnfh6gzc0d88d6mjmu7. https://explorer.bitquery.io/bitcoin/tx/3c4e8e98890fa5c633d2a4f853751513e0a6558baa2318914eec73c727ef8316. This 1,119 BTC has since then not moved from this wallet and can hence be considered to still be in possession of the US Government.
However the tokens transferred from 361yogPsasxJz6JAaFskmWZes14Gs38ikj to 10 different wallets have been further sent to various other wallets. Utilising the money Flow API and the graphic visualisations, we were able to trace as many as 5 wallets holding over 10k+ in BTC. Let’s take a closer look at the money movement details for one of them
3FZ4YzmmKn3kFhV8gx65PbTigw9d1APK4g
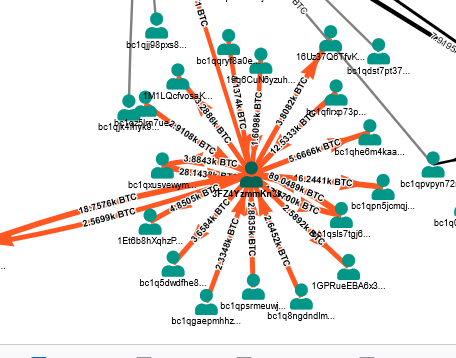
The account has over 1687 inbound transactions and 1717 outbound transactions both amounting to ~17k+ in BTC. The money flow from the receiver wallets follow a similar pattern.We pulled the in bound and outbound transactions data based on date filter using below query:
query ($network: BitcoinNetwork!, $address: String!, $inboundDepth: Int!, $outboundDepth: Int!, $limit: Int!, $from: ISO8601DateTime, $till: ISO8601DateTime) {
bitcoin(network: $network) {
inbound: coinpath(
initialAddress: {is: $address}
depth: {lteq: $inboundDepth}
options: {direction: inbound, asc: "depth", desc: "amount", limitBy: {each: "depth", limit: $limit}}
date: {since: $from, till: $till}
) {
sender {
address
annotation
}
receiver {
address
annotation
}
amount
depth
count
}
outbound: coinpath(
initialAddress: {is: $address}
depth: {lteq: $outboundDepth}
options: {asc: "depth", desc: "amount", limitBy: {each: "depth", limit: $limit}}
date: {since: $from, till: $till}
) {
sender {
address
annotation
}
receiver {
address
annotation
}
amount
depth
count
}
}
}
{
"inboundDepth": 1,
"outboundDepth": 1,
"limit": 10,
"offset": 0,
"network": "bitcoin",
"address": "3FZ4YzmmKn3kFhV8gx65PbTigw9d1APK4g",
"from": null,
"till": null,
"dateFormat": "%Y-%m"
}
A generic Bitquery API call was used to fetch information about outbound transfers first and then correlated this with the similar information from other accounts as well.
Apart from what we discussed for the silk road seizure, on March 7 2023, the Government moved 40k BTC, sending 9,825 to Coinbase to sell and 30,174 BTC to address.
Query used to fetch this data:
query ($network: BitcoinNetwork!, $hash: String!, $limit: Int!, $offset: Int!) {
bitcoin(network: $network) {
outputs(
txHash: {is: $hash}
options: {asc: "outputIndex", limit: $limit, offset: $offset}
) {
outputIndex
address: outputAddress {
address
annotation
}
value
value_usd: value(in: USD)
outputDirection
outputScriptType {
annotation
pattern
type
}
outputScript
}
}
}
{
"limit": 10,
"offset": 0,
"network": "bitcoin",
"hash": "d43068e021701606724af16aeb8197a3530021d45a16d5b830b465da6c5ce9e6"
}
bc1qf2yvj48mzkj7uf8lc2a9sa7w983qe256l5c8fs. As per the data this address can be considered a change address in transaction d43068e021701606724af16aeb8197a3530021d45a16d5b830b465da6c5ce9e6. This 30,174 BTC is considered to still be in possession of the US Government as there are no further outbound transactions from the account holding this BTC.
Unraveling the Silk Road Heist: From Fake Vendor Accounts to Ongoing Blockchain Investigations
For a quick background on where this token pool came from: James Zhong set up fake Silk Road vendor accounts solely for the purpose of laundering money, never actually listing anything for sale. Zhong funded the address associated with each vendor account with between 200 and 2,000 Bitcoin, and soon after would initiate multiple transactions to withdraw that amount in a matter of milliseconds.
By doing this several times over several days, he was able to trick Silk Road’s system into letting him withdraw more than he deposited, ultimately stealing 50,000 Bitcoin. Soon after the theft, Zhong consolidated his 50,000 Bitcoin in two wallets, with 40,000 Bitcoin in one and 10,000 in the other. The funds sat untouched for over a year, until he gradually moved them to new wallets over several years from October 2013 to May 2019. Between December 2020 and January 2021, Zhong also moved a portion of the funds to a mixing service in an effort to obfuscate the flow of funds.
Since the blockchain is forever, so data enthusiasts and investigators can always return to old, suspicious transactions and investigate them using the latest methods.
Unveiling Complex Transactions: Patterns in 30k BTC Holding and Intriguing Flows in the Blockchain
Intricacies within the blockchain continue to captivate our attention as we scrutinize the account bc1qf2yvj48mzkj7uf8lc2a9sa7w983qe256l5c8fs, which holds a steadfast 30,000 BTC, seemingly untouched. A striking parallel unfolds as observed in prior instances, notably when 8,925 BTC were intricately disbursed across 10 individual accounts. A similar pattern emerges with 9,825 BTC redirected to account (367YoRXht9x28BupqPaVnYfoM1xQP6XG4k) through transaction 53d14a37ac8f0a30f14dc061e4169cfbd65291d3cea540d366b292afc4802869.
Subsequently, 93.49 BTC fans out to 10 distinct accounts, each further subdividing funds into equal denominations. Notably, one wallet receives ~70 BTC not from the initial 8.9k BTC chain but from an additional 10 accounts, showcasing a fascinating repetition of denominations. The account (1H8vVaiKxaEG2vCDcQ7XuneoZMVk2fhgDu) also veils its holdings through indirect fund flows, adding another layer of complexity.
On March 14th, 2023 this enigmatic wallet received approximately 2.5k BTC, featuring a distinctive 476.71 BTC transaction (transaction details), intensifying the intrigue surrounding these intricate blockchain maneuvers
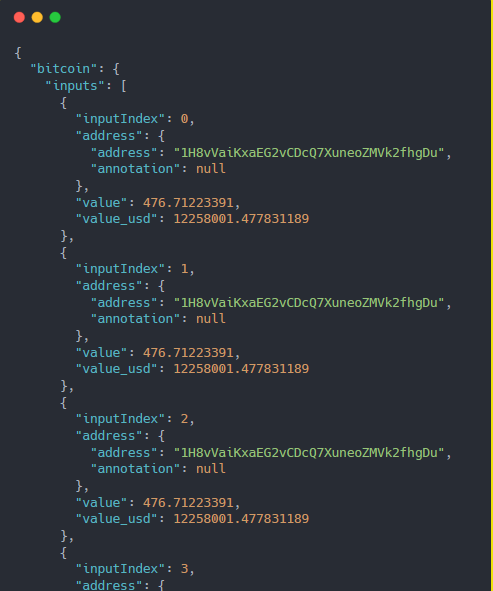
Reference data pulled from the API
As a conclusion, after July 12th, there has been some movement of funds in September amongst the wallets involved at level. While the wallets involved with the three culprit wallets during the 3 major seize events have had a lot of activity, however since the amounts are small and the fact that they are circulated across a multitude of wallets, it’s uncertain that indeed all these wallets are owned by the US government.
However, one things that’s sure is confiscations play a crucial role in combating crime associated with cryptocurrencies. It does ensure that it’s not used for any illegal and illicity activities. Though the tokens for the other hacks were seized and are still held by a small group of wallets, Bitfinex received $312,219.71 in cash and 6.917 BCH from the United States Department of Homeland Security (DHS) after the assets were stolen from the exchange. According to the US government agency, the total stolen bitcoin was valued at approximately $4.5 billion of which 94,000 bitcoin, valued at around $3.6 billion was recovered.
Conclusion
As we navigate the intricate web of cryptocurrency regulations and law enforcement, it becomes evident that blockchain technology not only underpins the decentralized nature of digital currencies but also serves as a powerful ally in the hands of those seeking justice. The ability to track and manage Bitcoin seized by the US government through blockchain data not only enhances transparency but also opens avenues for more efficient and accountable handling of seized assets. As we look to the future, the synergy between blockchain technology and legal frameworks promises to redefine the landscape of asset tracking and forfeiture, providing a glimpse into a more secure and regulated digital financial ecosystem.
The information provided in this material is published solely for educational and informational purposes. It does not constitute a legal, financial audit, accounting, or investment advice. The article's content is based on the author's own research and, understanding and reasoning. The mention of specific companies, tokens, currencies, groups, or individuals does not imply any endorsement, affiliation, or association with them and is not intended to accuse any person of any crime, violation, or misdemeanor. The reader is strongly advised to conduct their own research and consult with qualified professionals before making any investment decisions. Bitquery shall not be liable for any losses or damages arising from the use of this material.
Blog written by guest author Laisha
Subscribe to our newsletter
Subscribe and never miss any updates related to our APIs, new developments & latest news etc. Our newsletter is sent once a week on Monday.


