Do not be Fooled by Crypto Quiz Games!
What is the Quiz?
There are a number of “Crypto Quiz Games” smart contracts appearing in the Ethereum network. The game is simple: you have to guess the answer to the question. The prize is from 1 to 6ETH and even more.
Example is this one:
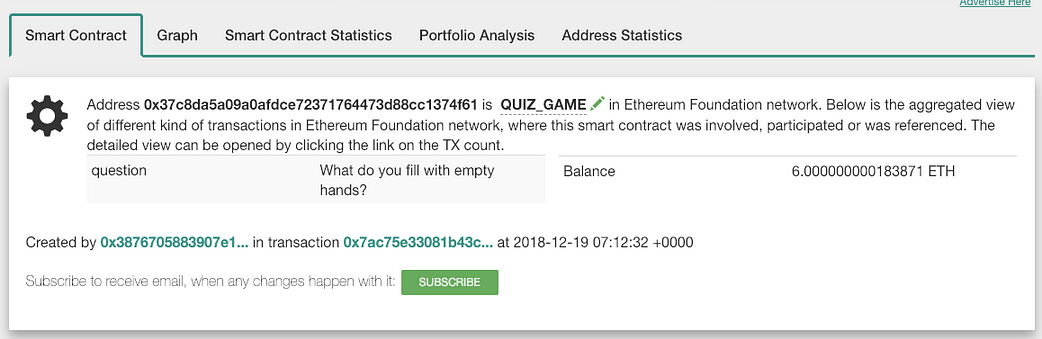
Example QUIZ_GAME ( source: Bloxy.info)
You can find sources of these contracts at Etherscan
Rules are simple: you can answer the question and the contract will compare the hash of the correct answer and your hash, and of they match, transfer you all the contract balance, which is at time of writing is 6 ETH. Not bad deal!
Oh, yes… almost forgot… to answer you have to deposit at the call minimum 3 ETH. So the cost of answer is 3 ETH and the prize is 6 ETH. Again, not a bad deal.
Also Read: FairWin Scam Smart Contract Coinpath Investigation
Easy Money
There are just 2 transactions in Etherscan at the time of writing: contract creation and set_game() call:
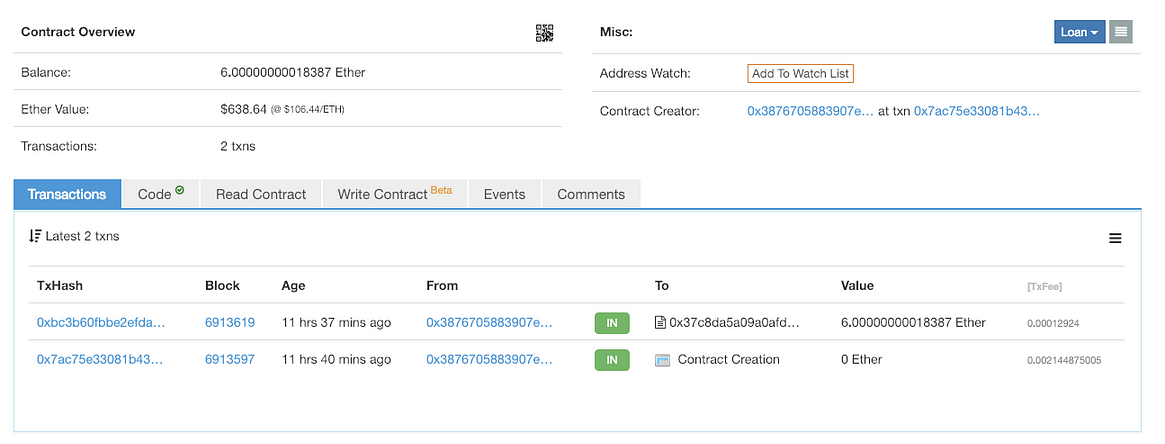
Only 2 transactions shown in Etherscan
The first one is just contract creation, and the second is set_game() call, sending 6 ETH to the contract as well. this one is pretty interesting, as it
SHOWS THE ANSWER TO QUIZ IN PLAIN TEXT!!!
If you open Etherscan:, switch call arguments to UTF-8 representation, you will see:
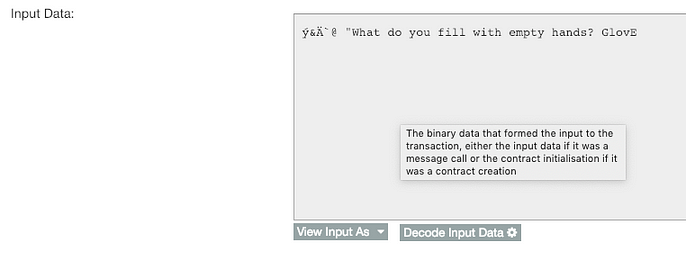
Source: Etherscan
This is even better shown in Bloxy.info:

Transaction details source: Bloxy.info
So it appears that you already get an answer (“GlovE”) and can easily get 3 ETH from the contract?
As you may guess, no.
Where is the Trap?
First, look at Bloxy detailed page of this contract, and you will see something different from Etherscan showing:
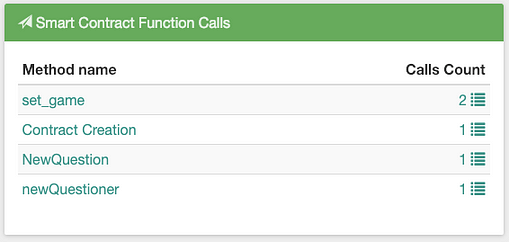
Smart contract calls Source: bloxy.info
What? You have more than 2 calls? And more than 2 transactions with smart contract? Yes.
Yes. The calls can be internal. When one smart contract calls another smart contract, they will be internal transactions, and they are equally important to see, as they also may change the internal state of the smart contract.
The creator of this smart contract looks as a cheater. He used another smart contract ( 0x4a3c2ead2a2ce2051e409ba51b710e4e09163492 ) to make internal calls, setting another answer hash, different from the answer, visible in Etherescan. It is done using this transaction:
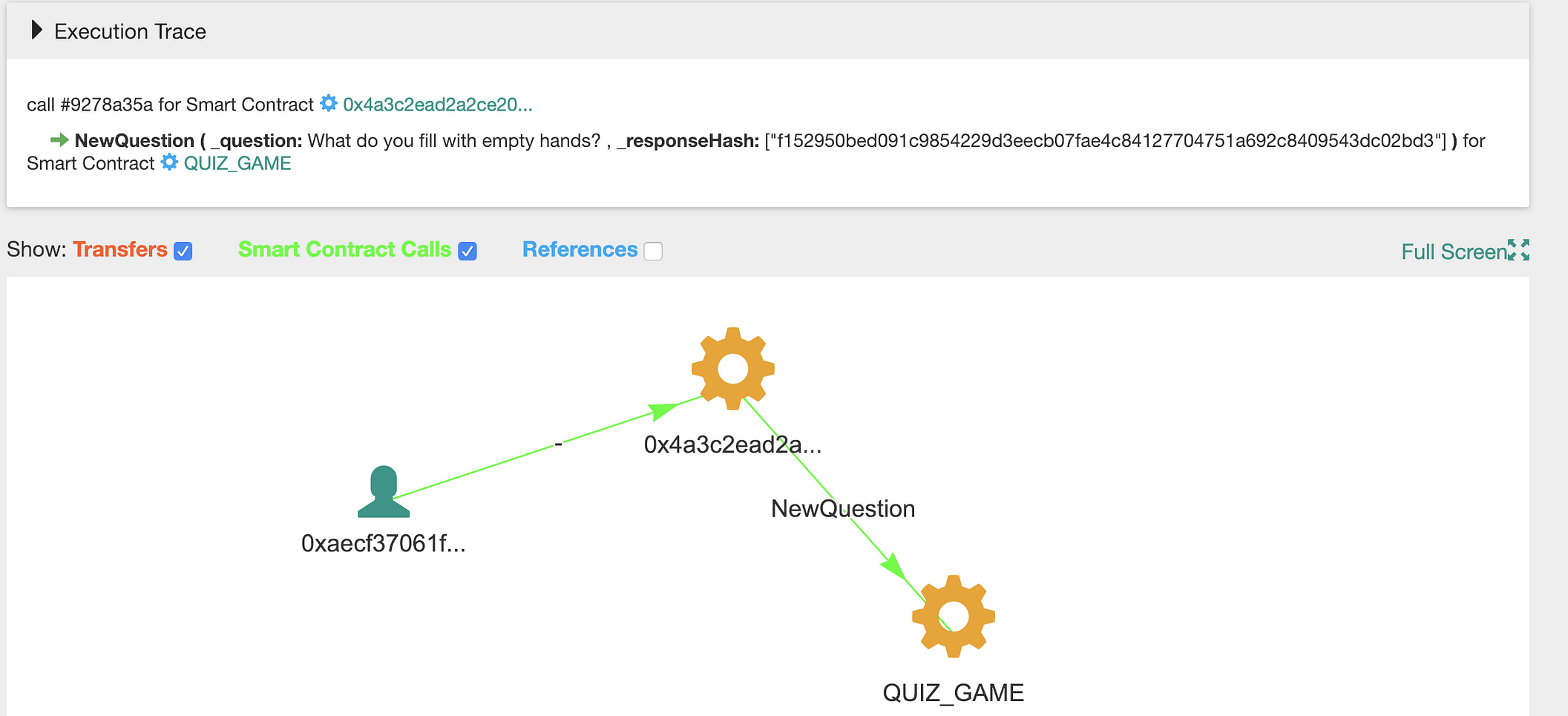
Question is the same, answer is not. Source: Bloxy.info
If you carefully look at the smart contract code, especially on the function set_game:
function set_game(string _question,string _response) public payable {
if(responseHash==0x0)
{
responseHash = keccak256(_response);
question = _question;
questionSender = msg.sender;
}
}
It only sets the answer hash (responseHash) IF and ONLY IF it was not set before. The creator of this smart contract used internal smart contract call ( not visible in Etherscan ! ) to change the answer hash.
responseHash is not intentionally shown as public smart contract variable. However, it can easily be fetched programmatically:
web3.eth.getStorageAt( Web3.toChecksumAddress(smart_contract_address),2).hex()
'0xf152950bed091c9854229d3eecb07fae4c84127704751a692c8409543dc02bd3'
As you see, it is equal to what is set in internal transaction, and is NOT equal to the hash of the “GlovE” answer, which is equal to:
web3.sha3(text='GlovE')
HexBytes('0x28a2cf3d43e08c03112de5742b068e23ab3cede00f14059427e6264859fd462c')
Totally different.
If you now look at Etherscan transactions, and will try to answer question, depositing 3 ETH, you will loose them.
So what is the right answer? Probably, it does not exist at all. The smart contract has this function:
function StopGame() public payable {
require(msg.sender==questionSender);
msg.sender.transfer(this.balance);
}
And the contract creator took care how he will use it, by making another internal transaction newQuestioner:
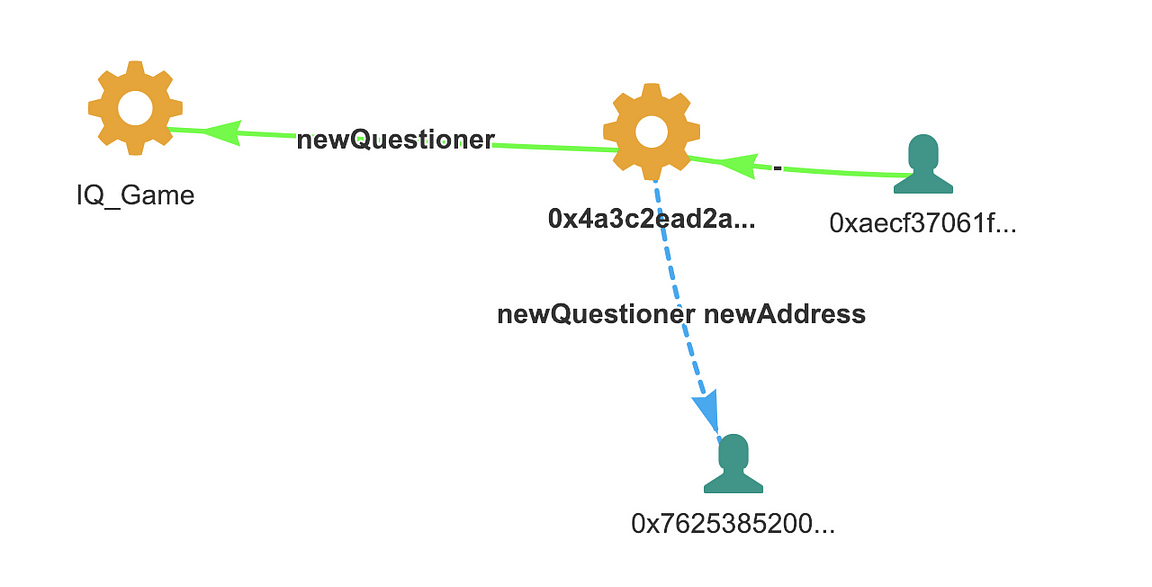
new Questioner source: Bloxy.info
So even if nobody will get the right answer, he will get all deposited money.
Scam Scheme
- Scammer creates Contract
- He calls methods of this new smart contract from another contract ( created by him specially ) to setup the question, answer hash and beneficiary. These calls are not visible in Etherscan!
- Then he calls external transaction (these are visible in Etherscan) with the same question and visible ( but wrong ) answer
- People looking at this transaction and on smart contract code, thinking this is an easy way to get the prize. They try to answer, deposit money and loose them
- After people deposited some money, scammer then can withdraw it.
How Many Victims?
The list of smart contracts, related to this particular , is quite large. The smart contract 0x4a3c2ead2a2ce2051e409ba51b710e4e09163492 is related to a good number of them:
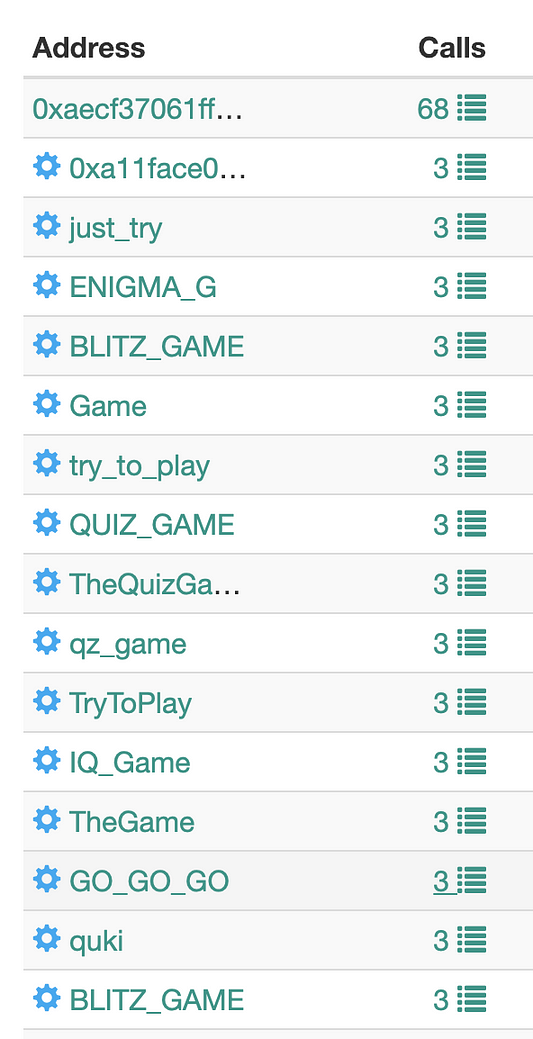
Source: bloxy.info
But how to get people involved in the scam? Probably the most evident way is to look of Try() method calls, where money where deposited to answer the quiz.
Bloxy shows the statistics of the method usage in all smart contracts by the name or signature. And the most successful are…
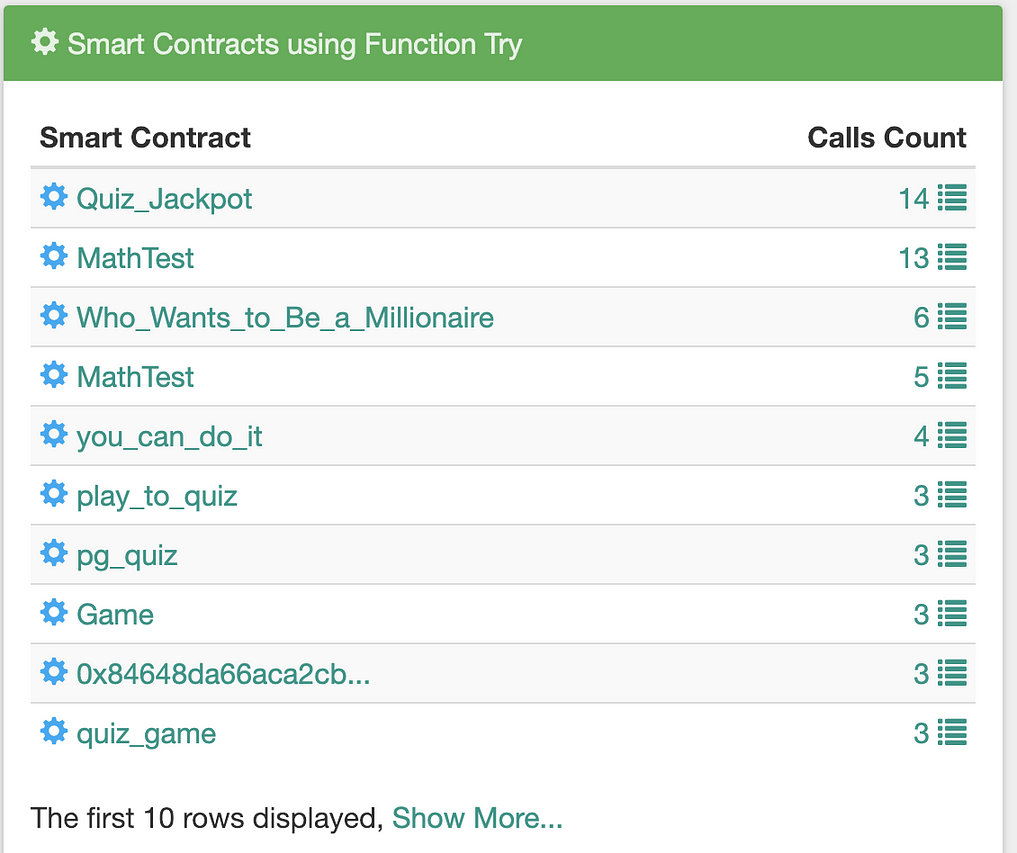
Try method usage in smart contracts. Source: bloxy.info
The statistics of how many times the Try(string _response) function was called, by months:
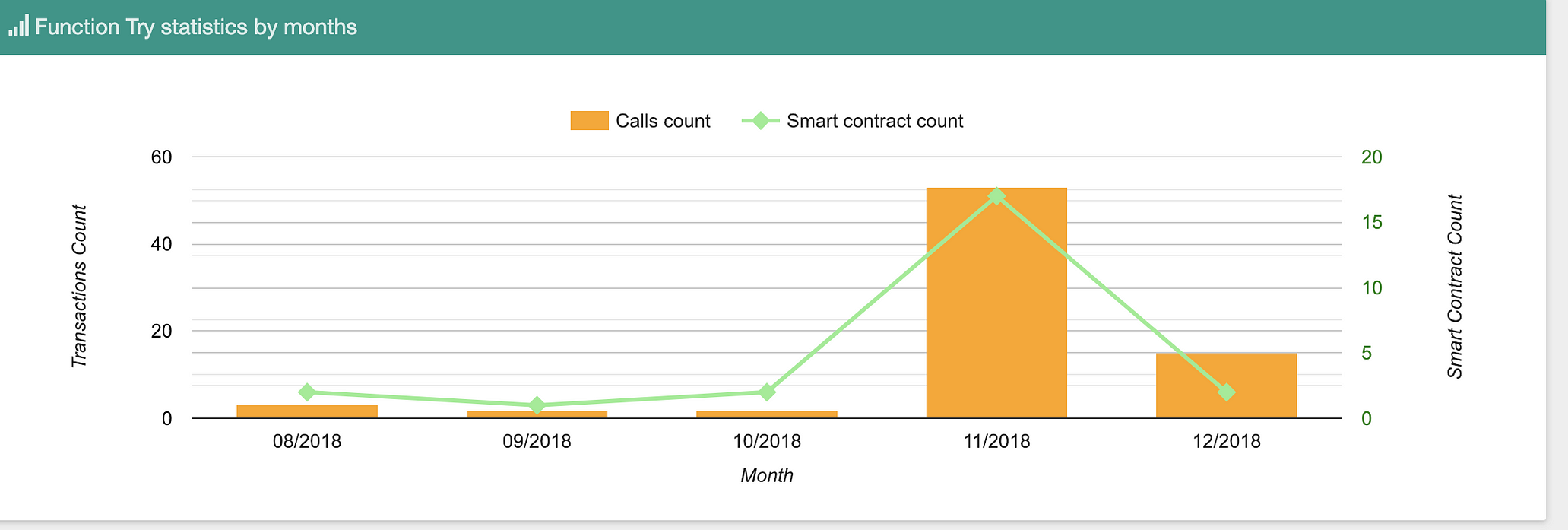
Scam is on the rise…Source: bloxy.info
In these calls, there is a fraction of “bait” calls, but there are real ones, where people trying to cheat using the visible answers from Etherscan, and lost their money.
Conclusions
We analyzed the scam example, mostly based on the fact, that Etherscan does not show the important information about internal transactions with smart contract. This allows cheater to fool people, who look at external transactions only. To prevent this in future, consider that:
- Easy money never exists. If you think you can fool somebody, most probable scenario is this is the bait of scammer
- Pay attention to internal transactions between smart contracts. In good developer hands, they are the powerful tool ( we will hopefully cover this in the future materials about DEX and derivatives ). Bad developers can cheat you with their smart usage.
- Consider using more information about the smart contract transactions, and Bloxy.info is a great resource for that. Etherscan shows not all transactions, coming to the smart contract.
- Keep your money in your pocket 🙂
Subscribe to our newsletter
Subscribe and never miss any updates related to our APIs, new developments & latest news etc. Our newsletter is sent once a week on Monday.


