
Recovering Scammed Bitcoin: A Step-by-Step Guide
In the ever-evolving landscape of digital finance, the rise of cryptocurrency has brought both innovation and, unfortunately, new challenges. One such challenge is the prevalence of scams targeting Bitcoin owners, leaving victims to struggle with the loss of their hard-earned money. This comprehensive article will serve as a guide to those who have unfortunately fallen victim to Bitcoin scams, providing a step-by-step roadmap towards recovery of the stolen funds.
Common Bitcoin scams
Bitcoin and other cryptocurrency users in the web3 space can encounter various scams, and it is crucial to stay vigilant to protect yourself against potential threats.
Some common scams include:
-
Phishing Scams: This is a type of scam where a fraudster creates a fake website or emails that mimic legitimate platforms or influencers to trick users into revealing their private keys, sensitive information or login credentials. Phishing is one of the most common methods used in bitcoin scamming. A report by Chainalysis shows that over $374 million in crypto was stolen as a result of targeted phishing scams as it sees explosive growth.
-
Giveaway Scams: One of the most common kinds of cryptocurrency frauds are giveaway scams. Frequently spotted on prominent social media platforms like YouTube and Twitter, this form of social engineering attack is used to convince you to send crypto to scammers.
-
Exit Scams: A cryptocurrency exit scam is when the developers of a cryptocurrency pull their funds + profits gained, abandoning the project and investors with huge token decline and red candlesticks. In some cases, this can occur with a centralized exchange where a dishonest cryptocurrency exchange may suddenly shut down, taking user's funds with them. This happened in the case of FTX and Sam Bankman-Fried
-
Fake Wallets: Fraudulent wallet apps or websites that claim to provide secure storage for cryptocurrencies but are designed to steal users' private keys.
-
Tech Support Scams: Scammers pose as customer support representatives, reaching out to users and claiming there is an issue with their crypto account. They then request sensitive information or access to the user's computer.
-
Malware and Ransomware: One of the most common and serious cyber-attacks involves ransomware, in which a threat actor locks an organization’s data with encryption until a ransom demand is met. These attacks are increasing not only in number, but also in severity. Bitcoin accounts for approximately 98% of ransomware payments. Whether an organization pays the ransom or attempts to recover the data independently, a clear understanding of bitcoin is essential for cyber incident response planning.
Recovery Steps
Bitquery offers specialized investigation services to track stolen crypto funds, employing cutting-edge blockchain analysis tools for funds tracking.
To get started;
You can also utilize Bitquery’s Money Flow tool on the explorer to track and visualize transactions on the account.
Using Money Flow in Bitquery
Here's how to:
- Enter an account address and select the blockchain network
Lets say we are using this address below which is on the Bitcoin Main Network bc1pdue3wxdphwkvp7a8kktf975wrks04etzhqjsz3tlgalj0ttj7dvqvxrxk6
- Click on the "Money Flow" section
-
Select either "Graph" or "Sankey", with "Graph" being the default option
-
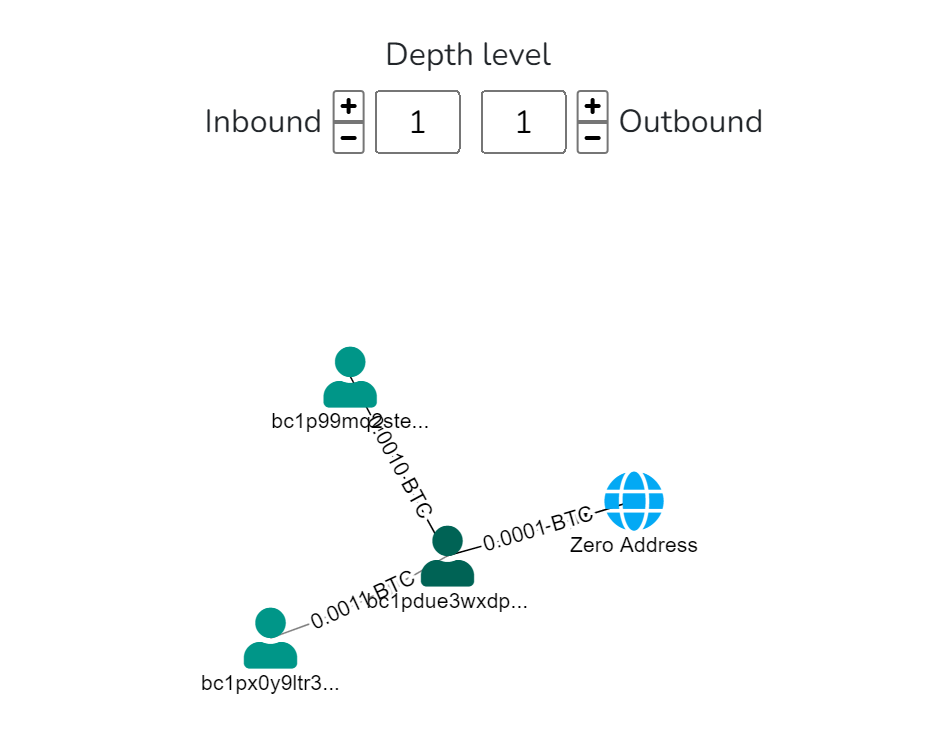
Use the “Depth Level” to set a degree of separation between transactions on the account/address. Depth Level helps to understand the flow of funds and understand the relationships between the addresses that receive the funds from the original address. The depth level has sliders (Inbound and Outbound) that you can increase or decrease to track and identify transactions within the account.
In a nutshell, Inbound = Funds that are coming in, while Outbound = Funds that are leaving
A typical simulation on the explorer will give you this ⬇
(We will only be using both inbound and outbound transactions)
Depth level 1: Transactions involving addresses directly connected to the initial address.
Depth level 2 and beyond: Extends the analysis to addresses associated with transactions at the previous depth level.
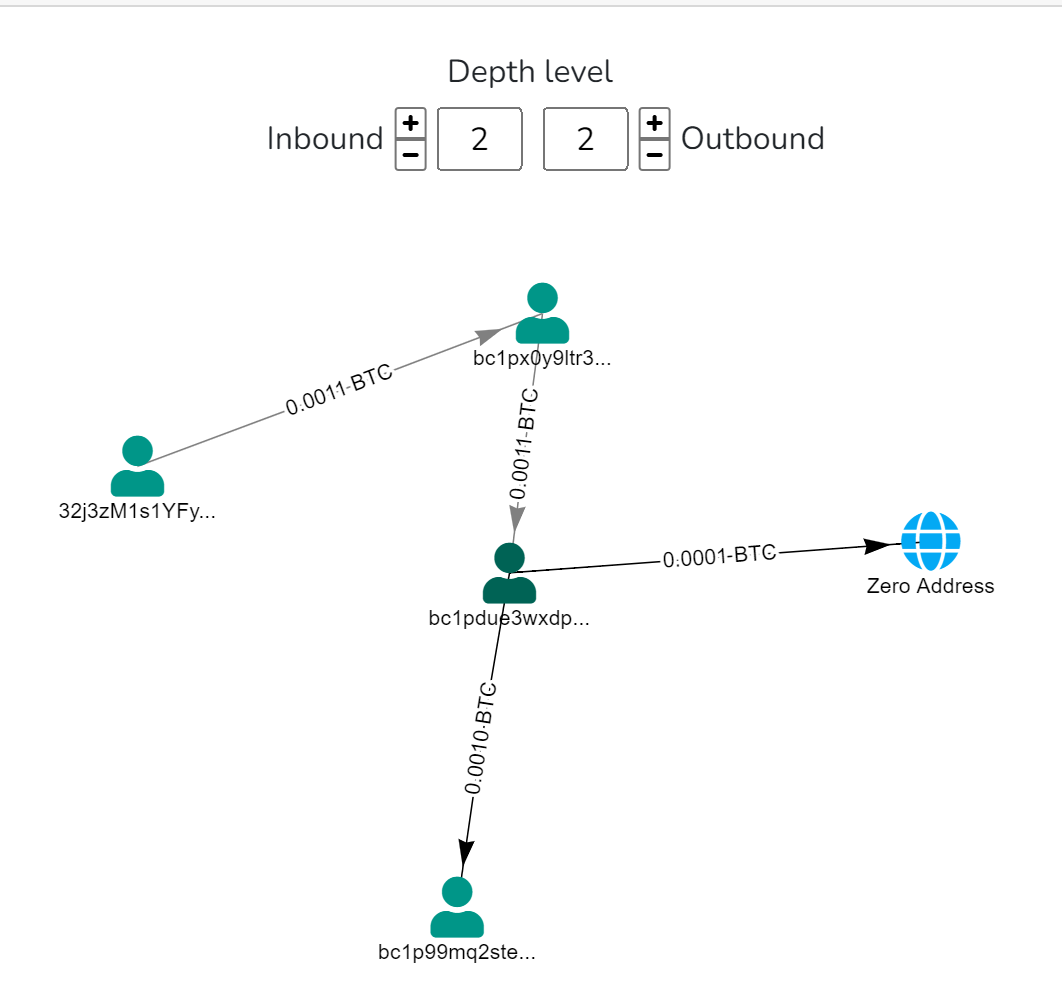
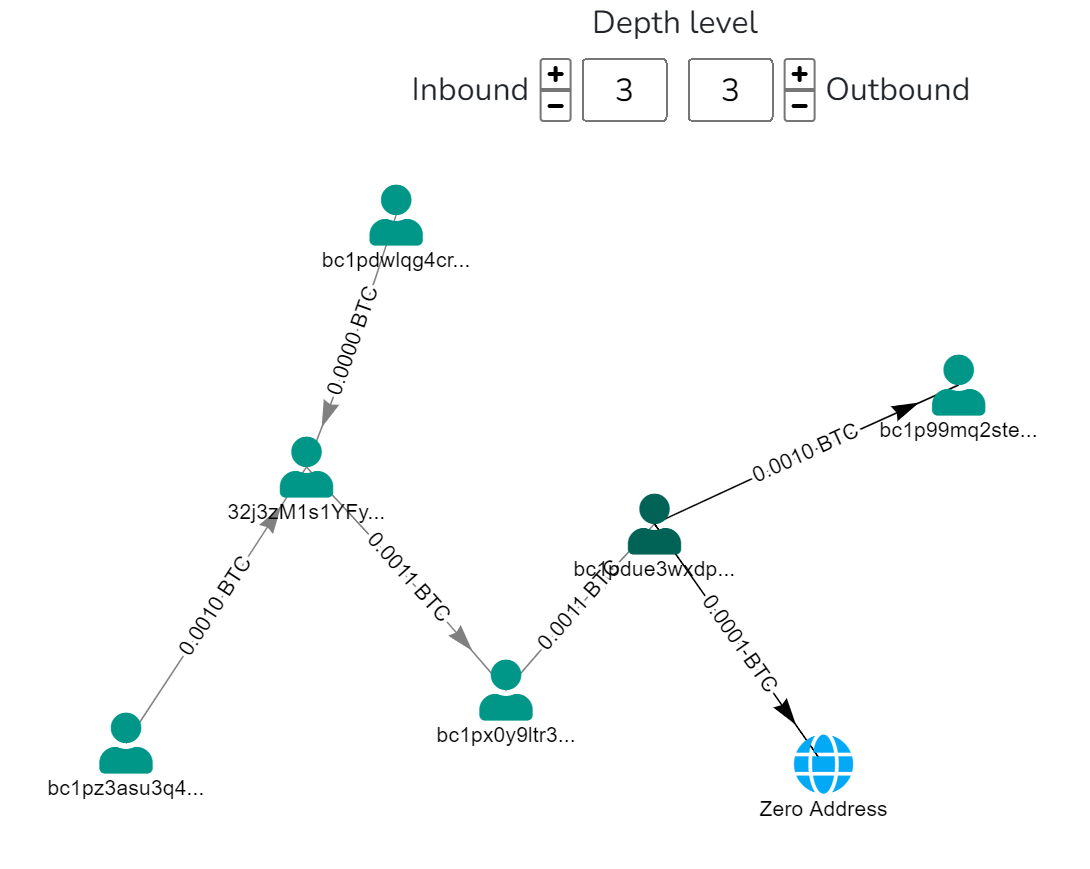
Depth level is a powerful tool when using Bitquery for account analytics, but it requires careful interpretation and context. Make sure to always consider external factors and aim for a holistic understanding of the transactional behavior involved with the original address and associated addresses.
Here is another example, in this comprehensive blog post, the United States Government Bitcoin Holdings, crypto assets and seizures were tracked and analyzed by utilizing the money flow tool from the Bitquery explorer.
Precautionary Measures
By adopting diligent precautions and safety measures, users can enhance their security and reduce the risk of falling victim to Bitcoin scams.
-
Secure Wallets: Use reputable wallets with strong security features. Also ensure you enable two-factor authentication (2FA) for an extra layer of security.
-
Beware of Phishing: Avoid clicking on suspicious links or emails. Double-check website URLs to ensure they are legitimate before entering any sensitive information. Use strong and unique passwords.
-
Cold Storage: Consider using hardware wallets or cold storage for long-term storage of significant amounts of Bitcoin. Keep private keys offline to prevent unauthorized access. DO NOT BUY HARDWARE WALLETS FROM THIRD PARTIES, make sure you are getting it directly from the company.
Some recommended hardware wallet providers are Ledger, Trezor and NGRAVE
-
Avoid Public Wi-Fi: Refrain from accessing your cryptocurrency accounts or making transactions using public Wi-Fi. Use a secure and private network for sensitive operations.
-
Secure Personal Information: Never share your private keys, passwords, or sensitive information with anyone. Always be cautious about the information you disclose online.
-
Diversify Investments: Avoid putting all your funds into a single investment or platform. Diversification can help minimize the impact of potential losses
-
Stay updated on the latest security threats and best practices in the cryptocurrency space.
Conclusion
In the dynamic world of crypto, scams targeting Bitcoin owners are a harsh reality. This guide aims to help victims recover stolen funds with a step-by-step approach.
Cryptocurrency scams like phishing and fake wallets are prevalent, making vigilance and preventive measures crucial. Bitquery provides hope for recovery through advanced blockchain analysis and expert consultation.
To stay safe, use secure wallets, beware of phishing, opt for cold storage, and diversify investments. Education and vigilance are our best defenses in this evolving crypto landscape. Stay secure, stay informed, and protect your assets.
The information provided in this material is published solely for educational and informational purposes. It does not constitute a legal, financial audit, accounting, or investment advice. The article's content is based on the author's own research and, understanding and reasoning. The mention of specific companies, tokens, currencies, groups, or individuals does not imply any endorsement, affiliation, or association with them and is not intended to accuse any person of any crime, violation, or misdemeanor. The reader is strongly advised to conduct their own research and consult with qualified professionals before making any investment decisions. Bitquery shall not be liable for any losses or damages arising from the use of this material.
Blog written by author Eugene Nnamdi
Subscribe to our newsletter
Subscribe and never miss any updates related to our APIs, new developments & latest news etc. Our newsletter is sent once a week on Monday.


