
A Deep Dive into Crypto Money Laundering and How Analytics Can Help
Crypto money laundering embodies the digital evolution of financial crime, using the anonymity and global reach of cryptocurrencies to obscure illicit gains. Unlike traditional methods that navigate through banks and casinos, crypto laundering thrives in a decentralized network, complicating tracking and regulation. The opacity of blockchain and the mix of centralized (CEXs) and decentralized exchanges (DEXs) challenge the identification of illicit flows.
A report by Nasdaq highlighted over $3.1 trillion in illicit funds circulating globally in 2023, underlining the magnitude of financial crime from activities like drug trafficking and terrorist financing.
Centralized exchanges (CEXs) present a structured yet vulnerable landscape for money laundering, where sophisticated multi-stage processes are employed to obscure the origins of illicit funds, despite regulatory efforts to enhance transparency and security. Decentralized exchanges (DEXs) make it difficult to reduce money laundering, by offering greater anonymity and minimal oversight, thereby enabling tactics to blur the lines between legitimate and illicit financial activities.
Decoding Crypto Money Laundering
The fight against crypto money laundering requires a nuanced understanding of the methods utilized across both centralized and decentralized platforms
Money Laundering on Centralized Exchanges (CEXs)
-
Placement: Introducing illicit funds into the system via cryptocurrency purchases or deposits.
-
Layering: Executing complex transactions to disguise fund origins, using trade-based techniques and high-frequency trading to muddle traceability.
-
Integration: Withdrawing laundered funds to external wallets or converting them into fiat, appearing as legitimate assets.
Money Laundering on Decentralized Exchanges (DEXs)
Swap and Mix: Using DEXs to exchange illicit tokens for other cryptocurrencies or stablecoins, employing automated market makers (AMMs) for trade execution.
Cross-Chain Hopping: Moving funds across blockchains to exploit varying anonymity levels and security protocols, further complicating tracking.
Tornado Cash facilitates laundering by breaking the on-chain link between source and destination addresses through deposit pooling, zero-knowledge proofs for anonymous withdrawals, and the use of relayers to further anonymize transactions.
The Scale of Laundering
Chainalysis reported that illicit addresses sent $22.2 billion in cryptocurrency to services in 2023, down from $31.5 billion in 2022. This decline indicates the impact of regulatory and law enforcement efforts but also underscores the adaptability of laundering techniques in response to these pressures.
The technical sophistication and rapid evolution of laundering methods in the cryptocurrency space demand equally advanced and dynamic countermeasures. This includes the development of more nuanced analytical tools capable of detecting and analyzing the complex patterns of illicit transactions, as well as a collaborative effort between regulatory bodies, financial institutions, and technology providers to address the challenges posed by these decentralized and often borderless financial activities.
Real-World Examples of Laundering in Crypto
Several high-profile cases illustrate the scale and sophistication of crypto money laundering:
-
The Lazarus Group: This North Korean state-sponsored hacking group is implicated in numerous cyber heists, including the infamous $281 million theft from the KuCoin exchange and the $600 million Ronin Hack. Laundering tactics involved moving stolen assets through a series of wallets and exchanges, eventually utilizing mixers like Tornado Cash to obfuscate the funds' origins.
-
The Silk Road: This dark web marketplace facilitated over $1 billion in illegal transactions, primarily in cryptocurrencies. Law enforcement's efforts to trace and seize these funds highlighted the early challenges and the eventual advancements in blockchain analysis techniques.
-
The PlusToken Scheme: One of the largest Ponzi schemes in history, PlusToken scammed billions of dollars worth of cryptocurrency from investors. The subsequent laundering of these funds involved sophisticated techniques, including the use of dummy accounts and a web of transactions across multiple platforms.
The Largest Breach
In March 2022, the Ronin Network, associated with the popular blockchain-based game Axie Infinity, fell victim to a sophisticated hack, leading to a staggering loss of approximately $622 million in Ethereum (ETH) and USDC.
This breach is attributed to the Lazarus Group, a notorious collective with ties to North Korea, known for their advanced cyber capabilities and involvement in significant global cyberattacks.
Tracking the Trail
The technical sophistication of the Ronin Network hack lies in its exploitation of the network's validator nodes. The Ronin Network operates on a set of nine validators, with a transaction requiring the approval of a majority (five) of these nodes. The attackers managed to gain control over five validators, four of which were directly controlled by Sky Mavis, the creators of Axie Infinity, and one belonging to a third-party Axie DAO. This was achieved through a combination of social engineering and exploiting security vulnerabilities, including the use of compromised private keys.
The compromised keys allowed the attackers to authorize two fraudulent withdrawals, effectively draining the Ronin bridge of 173,600 ETH and 25.5 million USDC. The breach went unnoticed for six days until a user's attempt to withdraw 5,000 ETH from the bridge revealed the shortfall, prompting an investigation that uncovered the extent of the theft.
Visualizing the Breach
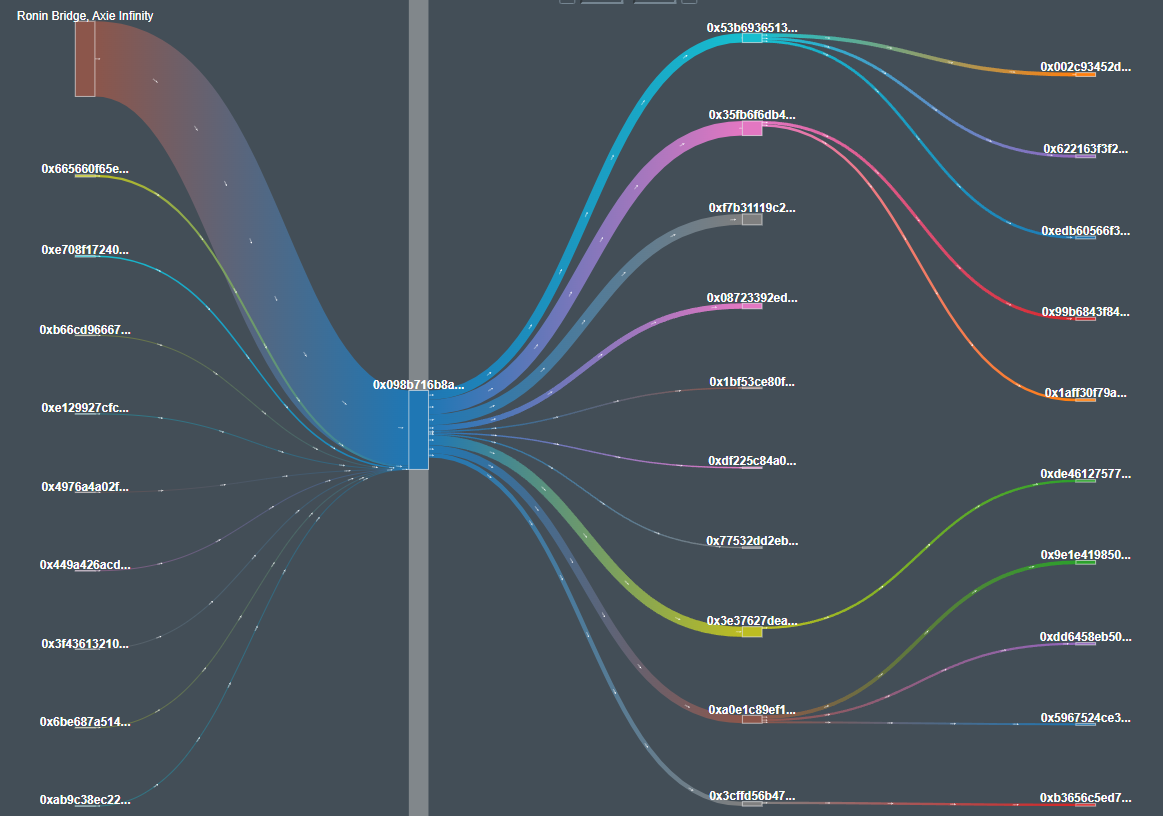
Below is a Sankey Diagram for the Ronin Bridge Exploiter Wallet. The various funding sources can be seen. The distribution of the stolen eth into various intermediary wallets can be seen in the next layer of the diagram after which the eth in sent to mixers in various batches.
https://explorer.bitquery.io/ethereum/address/0x098B716B8Aaf21512996dC57EB0615e2383E2f96/graph
(Asset- ETH, Depth Level : Inbound- 1 Outbound- 1, Detail Level- 10, Sankey)
Below is a Graph for the Ronin Bridge Exploiter Wallet. The various funding sources for the wallet can be seen as incoming transactions to the wallet. The distribution of the stolen eth into various intermediary wallets can be seen as outgoing transactions from the wallet.
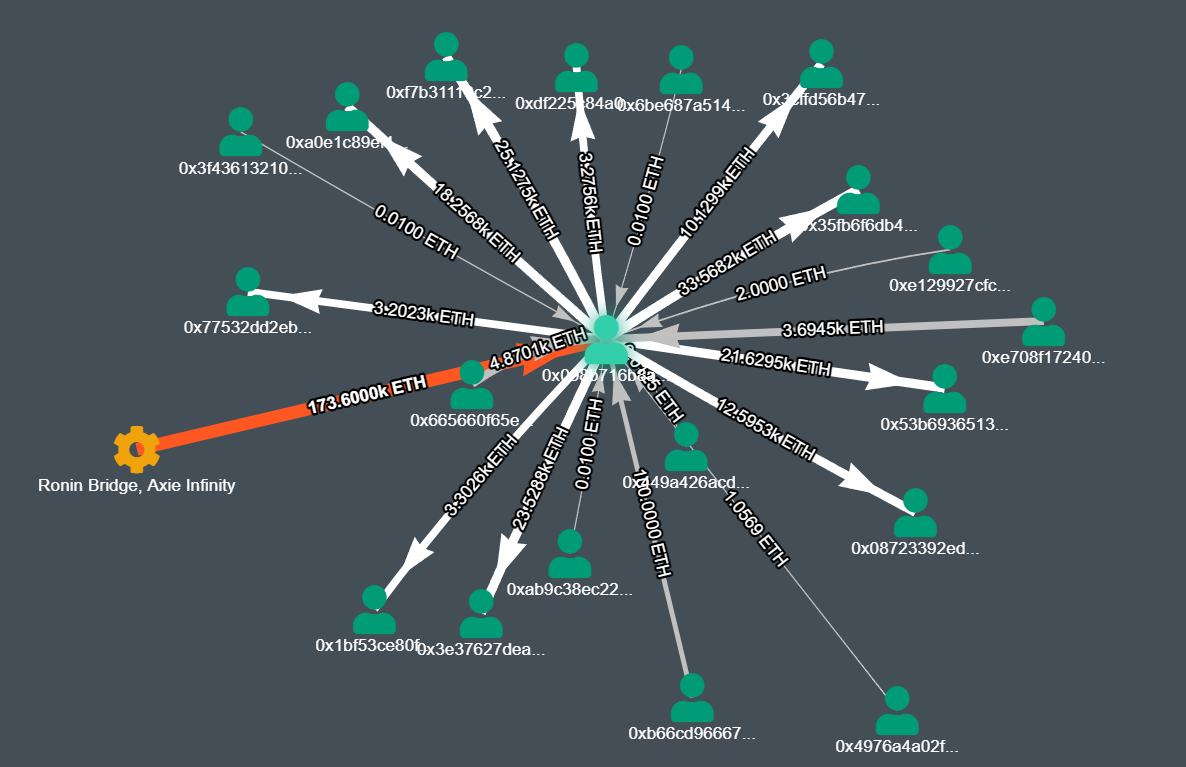
https://explorer.bitquery.io/ethereum/address/0x098B716B8Aaf21512996dC57EB0615e2383E2f96/graph
(Asset- ETH, Depth Level : Inbound- 1 Outbound- 1, Detail Level- 10, Graph)
Below is a Sankey Diagram for the Ronin Bridge Exploiter Wallet. The distribution of the stolen USDC into various intermediary wallets can be seen in this diagram.
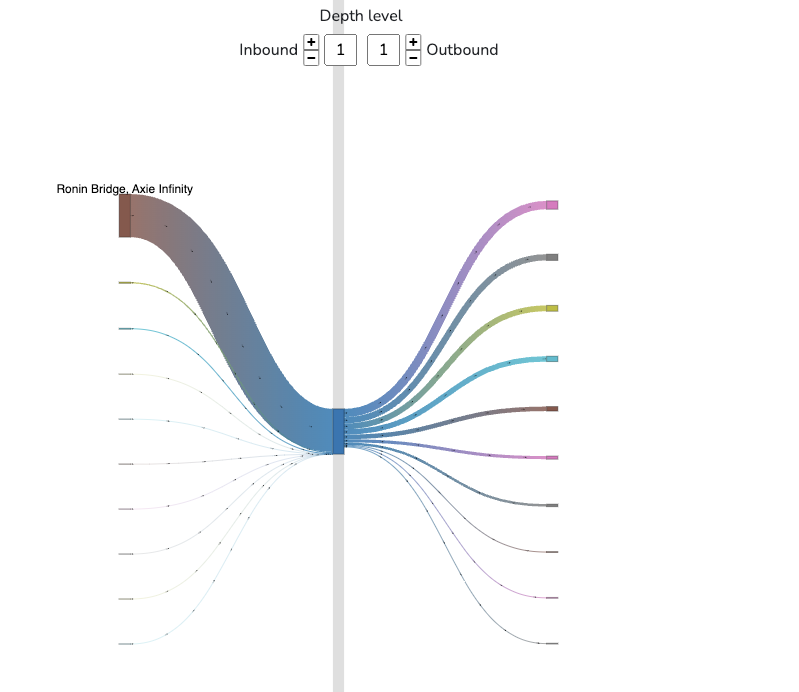
https://explorer.bitquery.io/ethereum/address/0x098B716B8Aaf21512996dC57EB0615e2383E2f96/graph
(Asset- USDC, Depth Level : Inbound- 1 Outbound- 1, Detail Level- 10, Sankey)
The distribution of the stolen USDC into various intermediary wallets can be seen in this diagram. The last layer of graph shows the wallets from which the USDC was converted to Bitcoin and subsequently passed through tumblers to make it difficult to track.
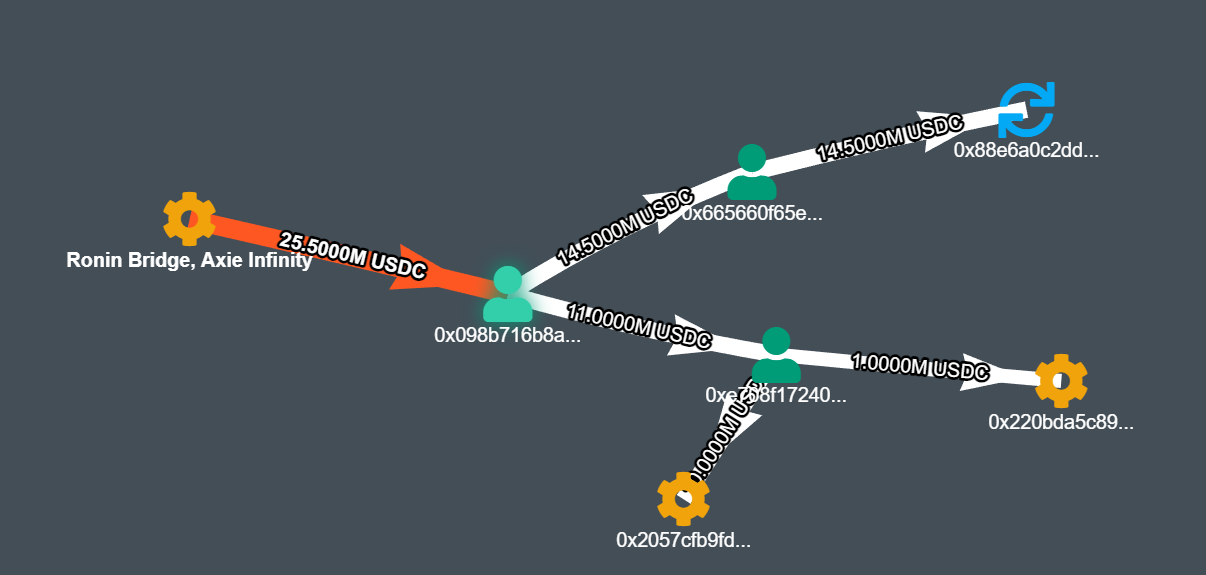
https://explorer.bitquery.io/ethereum/address/0x098B716B8Aaf21512996dC57EB0615e2383E2f96/graph
(Asset- USDC, Depth Level : Inbound- 1 Outbound- 1, Detail Level- 10, Graph)
Initially, assets were possibly moved through crypto mixers like Tornado Cash, which disrupts the traceability by mixing the stolen funds with others. Subsequently, these mixed funds might have been transferred to centralized exchanges (CEXs) for further obfuscation and possibly exchanged for different cryptocurrencies or fiat currency. The final step often involves withdrawing these assets to off-ramp points or into new, unconnected wallets, further complicating the tracking efforts.
The Ripple Effect
Approximately $35 million was recouped through asset seizures, employing sophisticated tracing methods to track the stolen funds to their withdrawal points. This collaboration with law enforcement and industry stakeholders enabled the quick freezing of assets. These recoveries account for about 10% of the total value stolen from Axie Infinity, adjusted for price fluctuations from the time of theft to recovery. This success underscores the increasing challenges that malicious actors face in converting their stolen cryptocurrency into cash. Effective collaboration between top-tier blockchain analysts, investigators, and compliance experts is proving crucial in thwarting the efforts of advanced hackers and money launderers.
Using the Bitquery’s Coinpath Tool to Analyze Money Flow
Coinpath addresses this need with its advanced set of API endpoints designed for blockchain money flow analysis.Coinpath APIs provide a powerful solution for tracing cryptocurrency transactions across more than 40 blockchains and their tokens. By offering detailed insights into money trails, Coinpath enables users to build a myriad of applications, from compliance tools to sophisticated investigation platforms, without the burden of maintaining extensive data warehouses.
Key Use Cases
Compliance: Essential for building KYT (Know Your Transactions) tools and adhering to Travel rules, Coinpath APIs facilitate the deanonymization of addresses, transaction monitoring, and risk analysis, enabling robust compliance solutions.
Investigation: Revolutionizing the approach to investigating cryptocurrency-related crimes (e.g. wallet thefts, scams), Coinpath APIs offer advanced capabilities for tracing money flows, proving indispensable for crypto investigation firms.
Getting Started
Bitquery Explorer: A beginner-friendly platform to explore blockchain data, allowing users to search addresses or transactions and view money flow data, just select an address or a token and click on the money flow tab. It's an ideal starting point to understand Coinpath APIs in action.
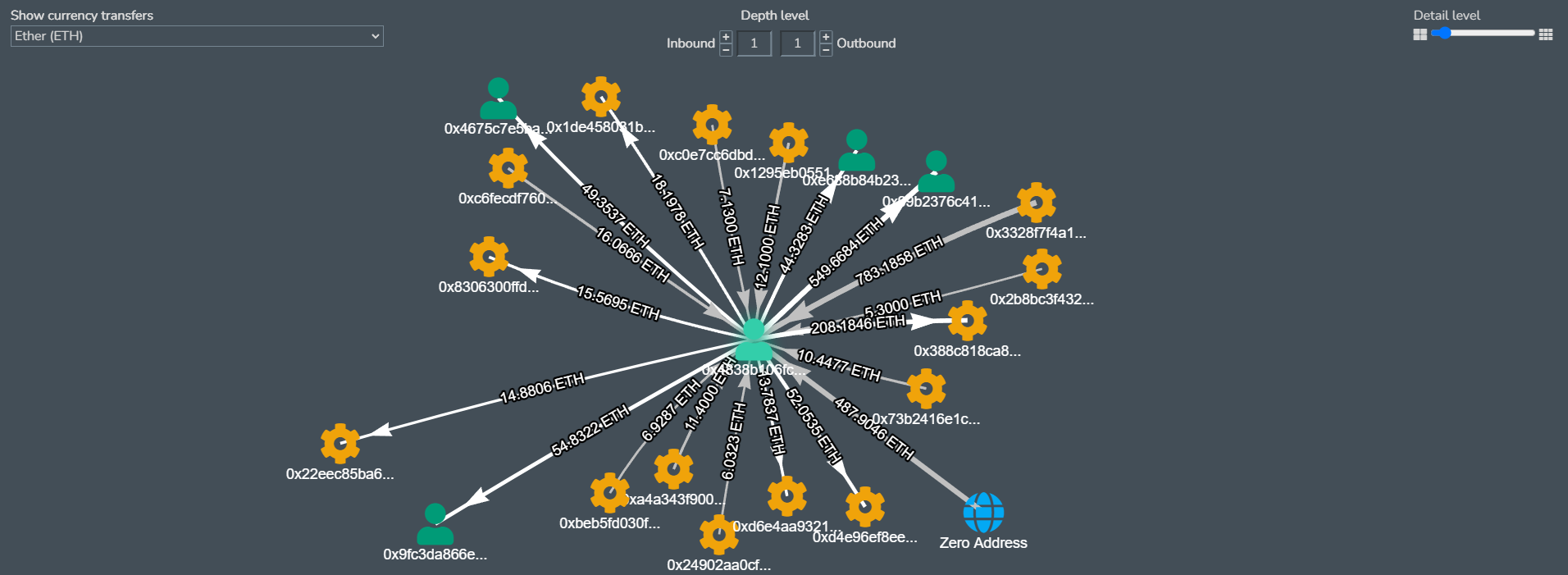
Let’s look at an example of the GraphQL IDE utilizing Coinpath
Example query UTXO coinpath with TX in/out values
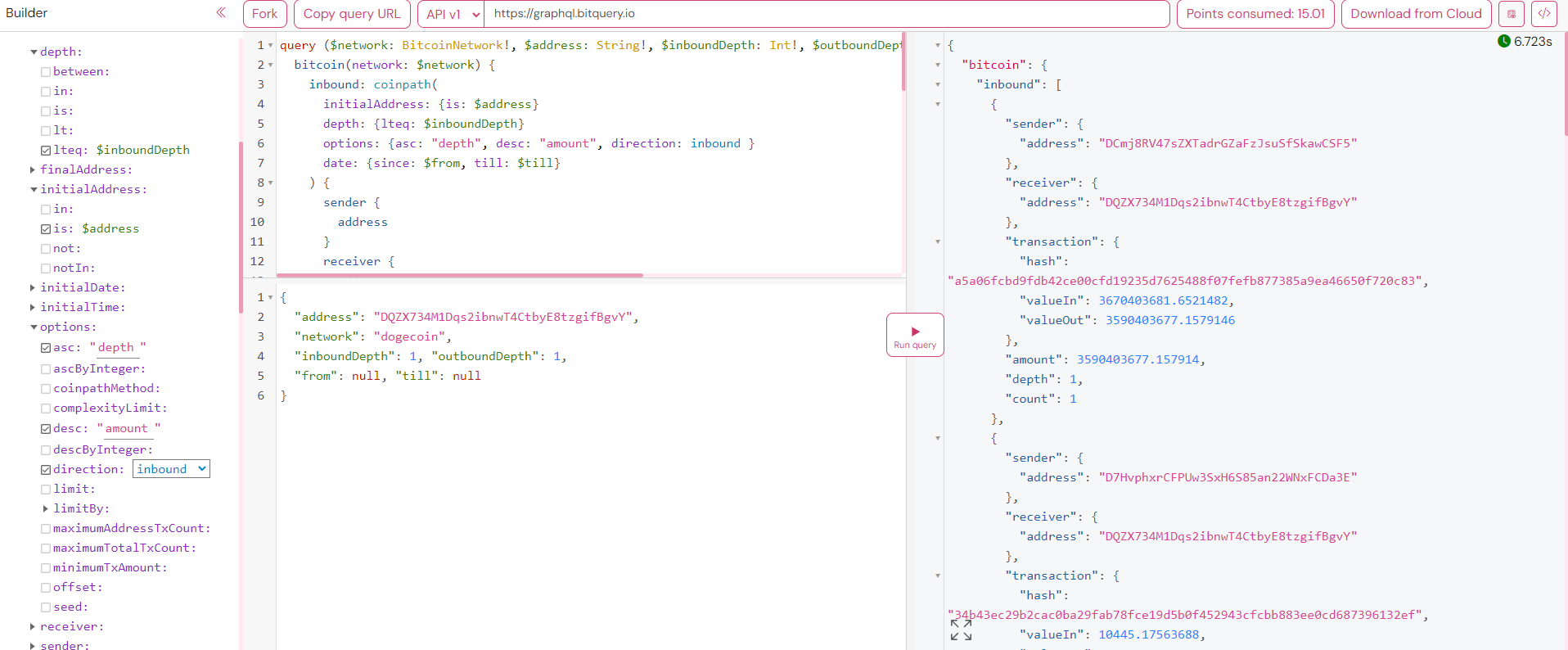
This query output reveals detailed transaction flows for a specific address, showcasing both incoming (inbound) and outgoing (outbound) transactions over a specified time frame.
How It Works
By using such a query, users can:
-
Trace Fund Origins and Destinations: It identifies where funds are coming from and where they are being sent to, making it crucial for transparency and accountability in financial transactions.
-
Investigate Financial Crimes: The data aids in the investigation of suspicious activities, such as money laundering or fraud, by revealing the flow of funds and connecting dots between different transactions and addresses.
-
Compliance Monitoring: For businesses and regulatory bodies, it's instrumental in ensuring compliance with KYC (Know Your Customer) and AML (Anti-Money Laundering) regulations by tracking the movement of funds to and from known addresses.
-
Risk Analysis: By analyzing the depth and count of transactions, companies can assess the risk profile of certain addresses or transactions, crucial for financial institutions and crypto exchanges.
Coinpath is designed to enhance and streamline the development of compliance tools, investigative applications, or any blockchain data project. Supporting over 24 blockchains, it offers a ready-to-use data infrastructure, saving time and resources for its users. For a detailed look at Coinpath MoneyFlow and its capabilities, visit the official page at Bitquery.
At the core of Bitquery's Crypto Investigation services is a comprehensive approach to the investigation and recovery of stolen cryptocurrencies. Recognizing the unique nature of each case, Bitquery tailors its services to address the specific needs of each client. These services include:
- Funds Tracking: Leveraging their proprietary blockchain analysis tools, Bitquery excels in tracing stolen funds across the digital landscape. This capability is pivotal in the recovery process, providing a clear pathway to the assets' current location.
- Legal Support: Bitquery's team includes seasoned crypto-lawyers adept at navigating the complex legal framework surrounding digital assets. Their expertise ensures that all necessary legal actions are taken to support the recovery efforts.
- Recovery Assistance: Coordinating with cryptocurrency exchanges and law enforcement agencies is a critical step in the recovery process. Bitquery facilitates these interactions, advocating on behalf of their clients to ensure the best possible outcome for asset retrieval.
Bitquery's process is designed to be straightforward and transparent, providing clients with a sense of security and clarity throughout what can be a stressful experience. The process unfolds in three key stages:
Consultation: Initially, Bitquery focuses on understanding the client's unique situation. This initial consultation is critical for identifying potential recovery options and planning the investigation strategy.
Investigation: With a strategy in place, Bitquery's expert investigators use their advanced tracking tools and techniques. Their diligent approach ensures a thorough search for the stolen assets.
The Cat-and-Mouse Game
The battle against crypto money laundering is a dynamic and evolving challenge. As regulatory bodies and law enforcement agencies enhance their tools and techniques, so too do the criminals in their methods to evade detection. Bitquery's solutions, like Coinpath and Crypto Investigation Services, stand at the forefront of this battle, offering powerful weapons in the ongoing fight for financial transparency and integrity. These tools not only illuminate the dark corners of the blockchain but also serve as a deterrent to those who would use cryptocurrencies for illicit purposes.
The development and refinement of blockchain analytics tools are critical in tipping the balance toward a secure and transparent digital financial ecosystem. As the blockchain continues to mature, the collaboration between technology providers, regulators, and the global financial community will be paramount in safeguarding the promise of cryptocurrencies while mitigating their potential misuse.
Written by Anish Majumdar
Subscribe to our newsletter
Subscribe and never miss any updates related to our APIs, new developments & latest news etc. Our newsletter is sent once a week on Monday.


