
How Are Criminals Exploiting Crypto? A Deep Dive Into 2024's Top Crime Typologies
The world of cryptocurrency has seen exponential growth, but with it comes the rise of increasingly complex crypto-related crimes. In the first quarter of 2024 alone, $739.7 million worth of cryptocurrency was stolen through methods like phishing attacks, exit scams, and private key compromises. These figures highlight the growing sophistication of crypto crime, making it essential to recognize and address these evolving threats.
Understanding various crypto crime typologies is crucial for anyone in the digital asset space. By identifying the different methods criminals use to exploit the decentralized nature of cryptocurrency, law enforcement, businesses, and individual investors can better safeguard their assets.
This blog will explore 20 distinct crypto crime typologies, each illustrated with real-world incidents. Additionally, we will highlight the role of specialized tools in tracing and identifying these activities to provide a comprehensive view of crypto crime's continuously shifting nature.
Understanding Crypto Crime typologies
Cryptocurrency typologies refer to the patterns and methods used for financial crimes in digital currency. These include scams where fraudsters trick victims, hacks that breach security to steal assets, and "exit scams" where perpetrators vanish with investors' funds. Due to the decentralized and anonymous nature of cryptocurrencies, these crimes can be complex. Understanding these crime typologies helps recognize and prevent illicit activities, thereby protecting investments from emerging threats.
typologies for Financial Crime Detection
To detect financial crimes, we need to explore different crime typologies. Next, we'll examine these patterns and real-world examples.
1. Ponzi Schemes Using Cryptoassets
Ponzi schemes are fraudulent schemes that promise high returns with minimal risk, depending on new investors' funds to pay earlier ones. They typically collapse when they fail to recruit enough new investors, revealing their unsustainable nature.
Incident Overview: Gain Bitcoin Scheme
- Initiated: 2017
- Company: Variable Tech Pte Ltd
- Promise: 10% monthly returns on Bitcoin investments
- Collapse: Resulted in a loss of Rs 6,600 crore (~$825 million)
Scheme Overview: Amit Bhardwaj and his associates ran a scheme promising high returns through Bitcoin mining. The operation collapsed when it couldn't sustain payouts due to a dwindling number of new investors, leading to significant financial losses. The failure prompted numerous legal cases and investigations, with the Enforcement Directorate taking action.
Tracking the Scam’s Unfolding: In cases like the Gain Bitcoin Ponzi scheme, analyzing the flow of funds and identifying key players is crucial. Bitquery supports such investigations by providing comprehensive blockchain data analysis. By examining Ethereum smart contracts and transaction histories, investigators can detect suspicious patterns like abnormal money loops and artificial deposits.
2. Use of Non-Compliant or Unlicensed Exchanges
Non-compliant or unlicensed exchanges operate without proper regulatory oversight and often involve illegal activities, such as money laundering and fraud. These exchanges facilitate illicit transactions by providing a platform for criminals to exchange or launder cryptocurrency outside of legitimate financial systems. Their lack of regulation makes them attractive to those looking to evade detection.
Incident Overview: RG Coins
- Date: September 2020
- Conviction: Rossen Iossifov sentenced to 10 years in prison
- Impact: Nearly $5 million laundered; over $7 million defrauded from U.S. victims
Case Summary: Rossen Iossifov, owner of RG Coins, was convicted for laundering funds connected to a fraudulent online auction scheme. The AOAF Network used RG Coins to launder proceeds from fake auctions, defrauding around 900 U.S. citizens. Iossifov faced sentencing under the RICO and for money laundering, highlighting the severity of his crimes.
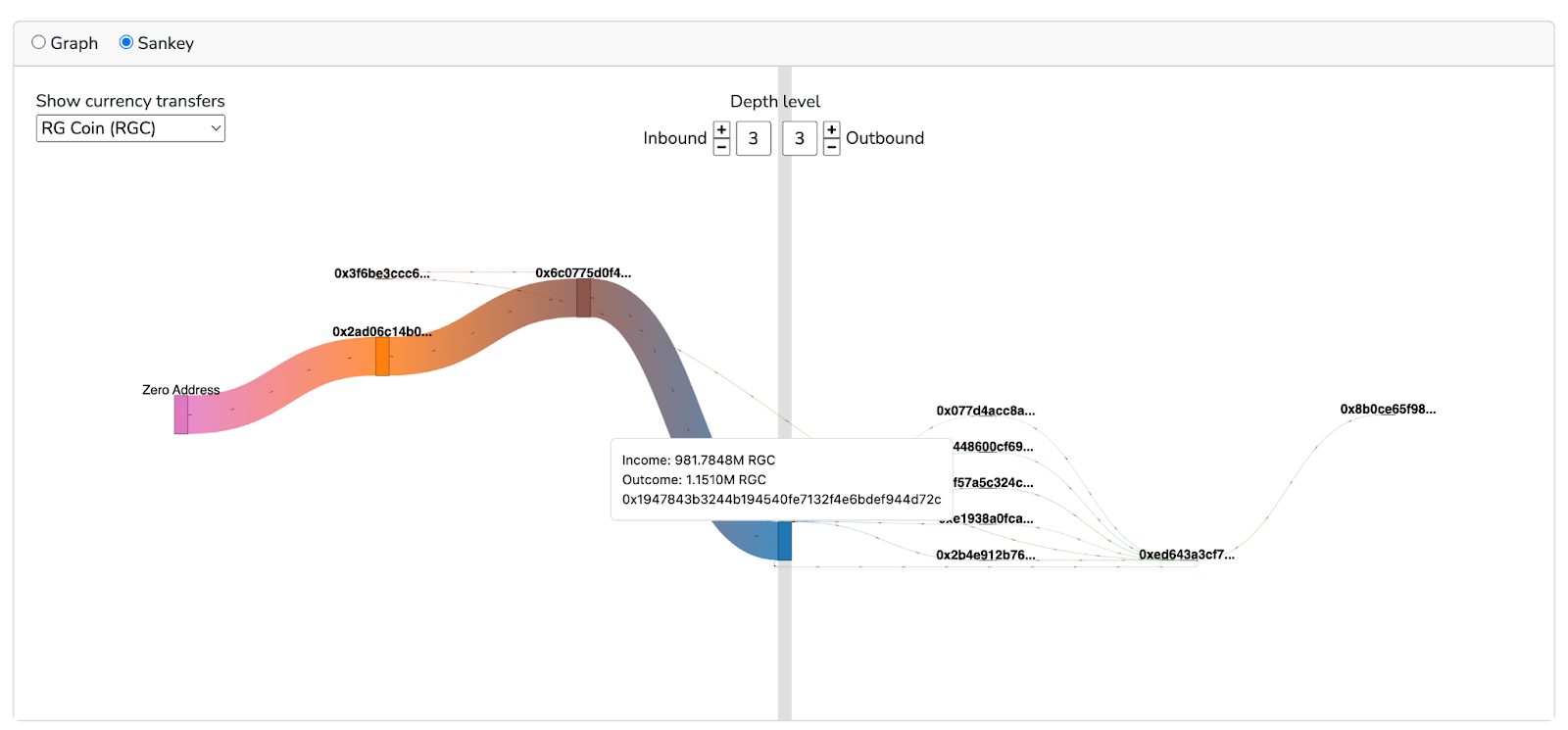
Tracking the Scam’s Unfolding: Tracking funds through non-compliant exchanges like RG Coins can be challenging with standard blockchain explorers. Traditional tools often require manual tracking of each transaction, which is time-consuming and prone to errors. Additionally, these tools lack annotations that could help identify key addresses or suspicious patterns, making it difficult to get a complete picture of the scam.
To effectively trace the flow of illicit funds, it’s essential to use advanced tools like Bitquery’s blockchain explorer and Coinpath API. These tools enable investigators to map out transaction flows, detect irregular trading behaviors, and monitor real-time deposits across multiple blockchain networks.
Bitquery empowers law enforcement and investigators to uncover the full extent of illegal activities on platforms like RG Coins, ensuring that the responsible parties are held accountable.
3. Cryptoasset Gambling
Cryptocurrencies in unregulated online gambling platforms can mask illicit funds and facilitate money laundering. These sites often scam users by promising high returns but failing to deliver, collecting substantial sums without oversight.
Incident Overview: E-Nugget Online Gaming Scam
- Date: 2022
- Details: ED seized Rs 19 crore from bank accounts and Rs 90 crore from crypto exchanges
Scam Overview: The E-Nugget app, posing as a legitimate gaming platform, vanished after collecting funds, leaving investors unable to access their money. The Enforcement Directorate (ED) seized nearly ₹90 crore from crypto accounts and ₹19 crore in cash. Key figures Aamir Khan and Romen Agarwal were arrested and are in judicial custody.
Tracking Funds
Tracking and recovering funds in crypto scams like the E-Nugget gaming fraud is challenging due to the complex and anonymous nature of transactions. Standard blockchain explorers often fall short, necessitating advanced tools for thorough investigation.
One significant problem is the difficulty in proving the legitimate origins of funds, especially when accounts are frozen or under dispute. Bitquery’s Digital Assets API offers detailed indexing and historical data for major cryptocurrencies including USDT and Ethereum. This data helps establish legitimate fund sources, especially when dealing with frozen accounts.
For instance, using a sample USDT contract address on Ethereum (0xdac17f958d2ee523a2206206994597c13d831ec7), you can:
- Track USDT Transfers Between Addresses: Use the USDT Transfer API to monitor the movement of USDT.
- Analyze Historical Price Data: Identify unusual trading patterns using the USDT OHLC Price Data API.
- Identify Major Token Holders: Find significant holders of USDT with the USDT Token Holder API.
Bitquery’s comprehensive tools combined with detailed reporting and legal support ensure effective tracking of stolen assets.
4. Chain Peeling
Chain peeling involves breaking down large illicit funds into smaller transactions across multiple addresses to obscure their origin and make tracking more difficult. This method is often used to launder money or evade detection by fragmenting the flow of funds, making it harder for authorities to trace the complete transaction history.
Incident Overview: Bitfinex Bitcoin Theft
- Year: 2016
- Theft: 120,000 Bitcoin stolen
- Outcome: Over $3.6 billion worth of Bitcoin seized
Case Summary: Hackers stole Bitcoin from Bitfinex, controlled by Ilya Lichtenstein and Heather Morgan. They laundered the funds using “chain peeling” breaking transactions and converting Bitcoin to other cryptocurrencies. Authorities have seized around $3.6 billion in stolen Bitcoin with Lichtenstein and Morgan charged with money laundering and conspiracy.
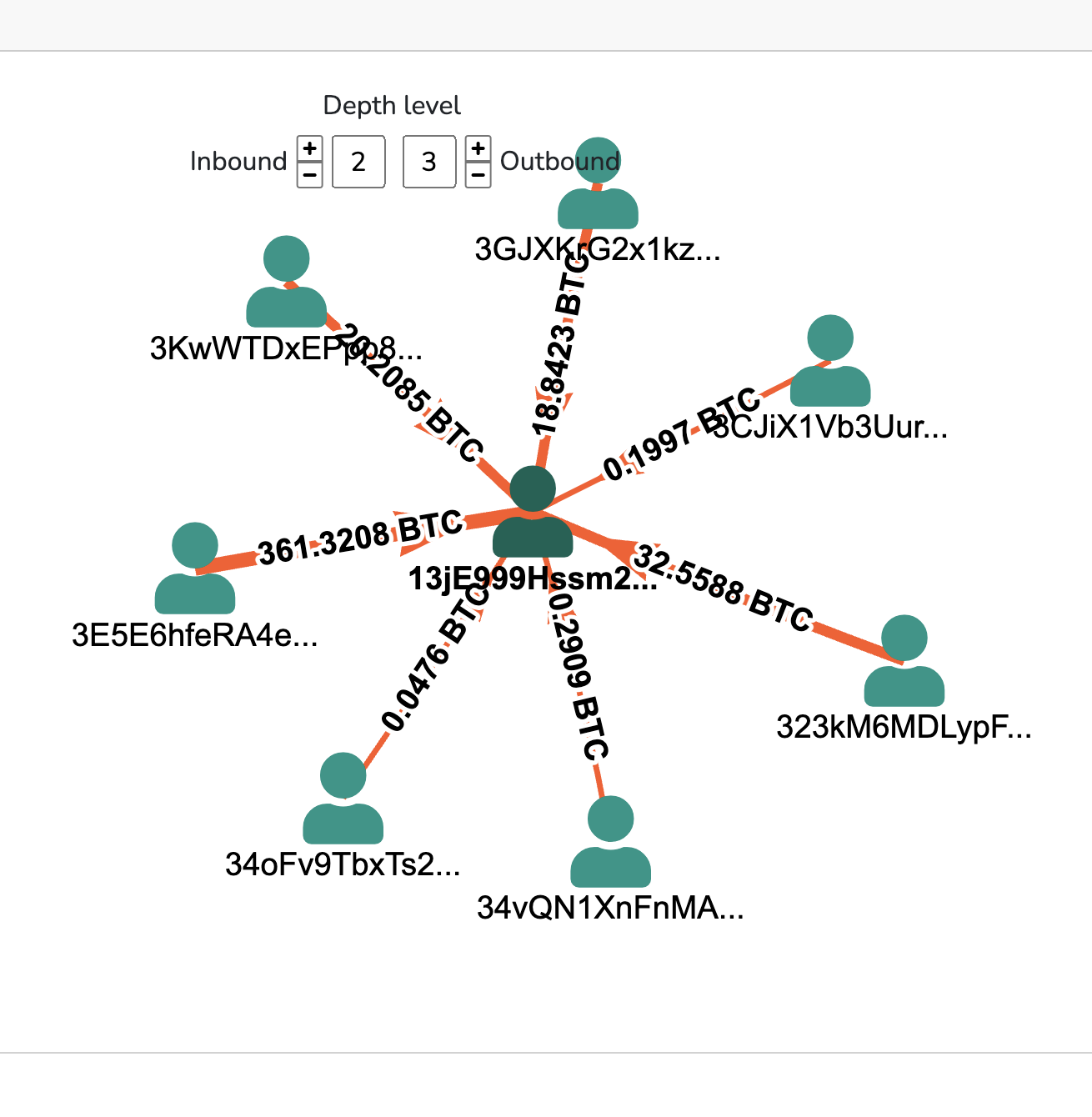
In this case, Two key addresses used by the hacker are identified. Let’s use Bitquery to analyze these addresses and gain insights into the movement of the stolen Bitcoin.
Address Analysis Using Bitquery
- Address A: 13jE999Hssm2GFf6Yob7zGCJtf1xnPPjHd
- Overview: This address received 433,468 BTC, representing a substantial portion of the stolen Bitcoin from Bitfinex. The entire balance has since been moved, leaving the address with a zero balance.
- You can explore the detailed movement of funds from Address A using Bitquery Explorer as shown below.
- Address B: 1J2Tem6ZSHnpppVhBpSq5pAZYmfjENqoD3
- Overview: Address B received 259.74 BTC from the stolen funds. On April 14, 2021, 6.51 BTC (about USD 412,317.90) was directly transferred to a prominent crypto exchange. The remaining funds were moved to three unidentified addresses which have not been active since.
- You can explore the detailed movement of funds from Address B using Bitquery’s Explorer.
5. Exchanges
Cryptocurrency exchanges can be exploited for laundering stolen or illicitly obtained crypto assets, particularly through decentralized platforms. These platforms often lack robust regulatory oversight, making them vulnerable to abuse for illicit activities.
Incident Overview: WazirX Wallet Hack
- Date: July 18, 2024
- Incident: Over $230 million stolen from a multi-signature wallet
- Outcome: Significant loss of assets and ongoing legal and financial complications
Attack and Response: WazirX lost over $230 million from a multi-signature wallet managed by Liminal. The breach led to reduced holdings and frozen assets, with criticism for the slow response. WazirX has initiated restructuring and sought legal protection under Singapore’s Insolvency Act.
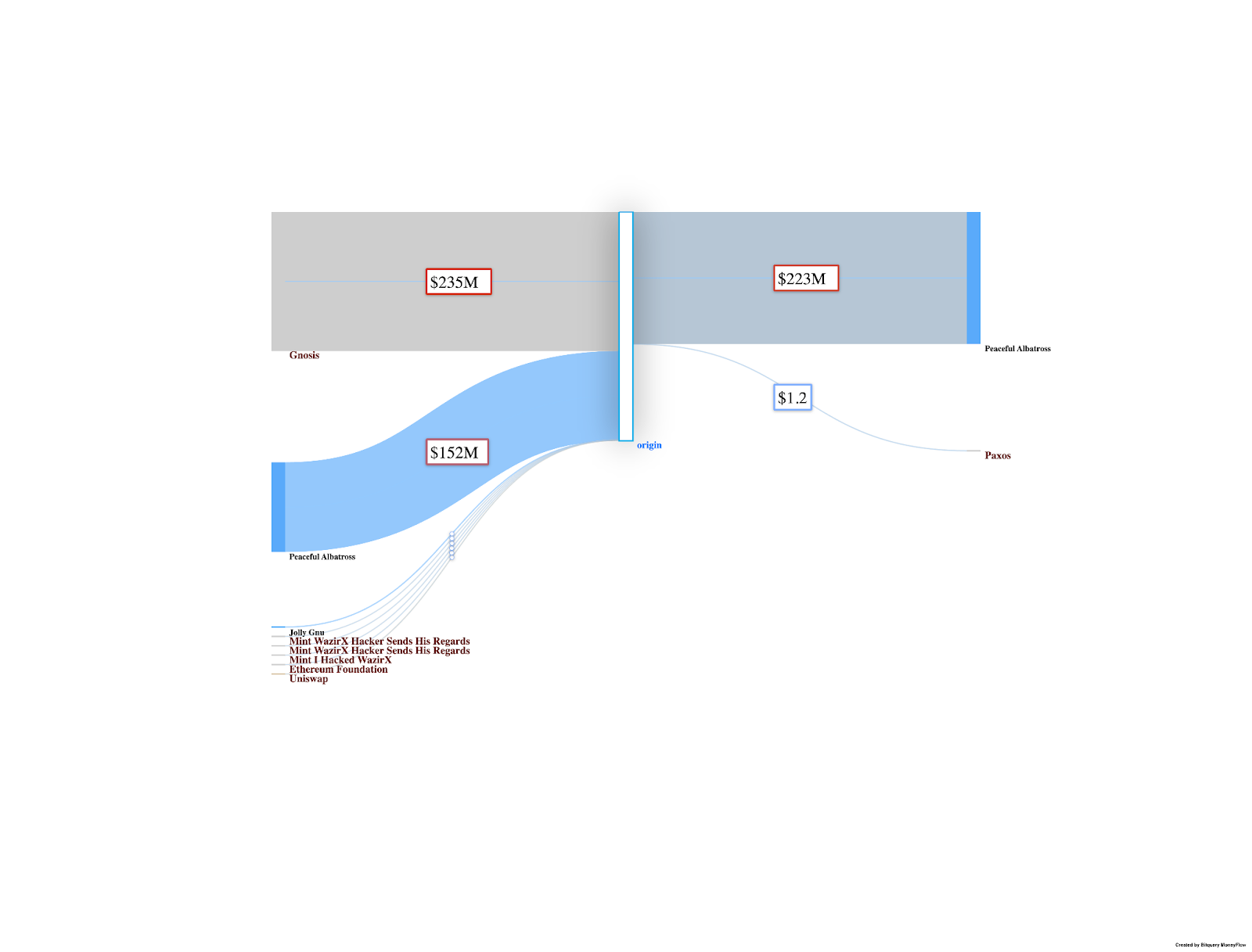
Attackers' Address: 0x6EeDF92Fb92Dd68a270c3205e96DCCc527728066
This address received 0.4795 BTC in 9 transactions, with a current balance of 0.3041 BTC. It has interacted with multiple related addresses.
Stolen Funds Moved Through Addresses:
- Address: 0x361384e2761150170d349924a28d965f0dd3f092
Received 43,800.36 ETH with no outgoing transactions, indicating funds have been held since July 18, 2024.
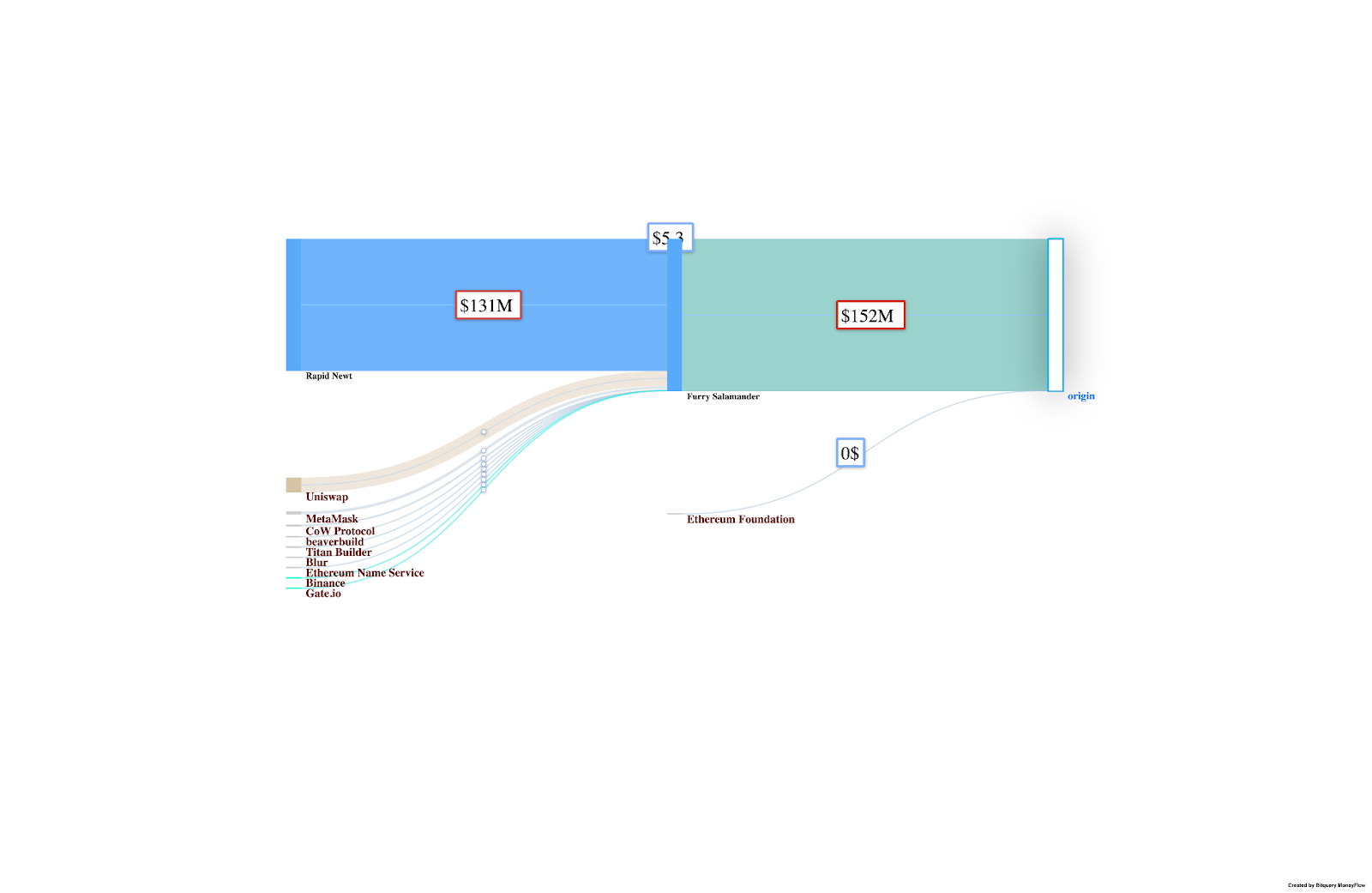
- Address: 0x04b21735e93fa3f8df70e2da89e6922616891a88
Received 15,306.69 in various currencies, with high transaction activity, including significant transfers involving WazirX assets.
Attack Transaction
- Transaction ID: 0x48164d3adbab78c2cb9876f6e17f88e321097fcd14cadd57556866e4ef3e185d
This transaction, executed on July 18, 2024, involved 0 ETH and a gas cost of $2.32, playing a key role in the attack's execution.
6. Crowd-funding through Charities and Other Organizations
Crowdfunding through fake charities uses the guise of legitimate non-profits to solicit cryptocurrency donations for illicit activities. This disguise allows them to raise significant funds while evading detection and complicating tracing efforts by authorities.
Incident Overview: Hamas' Use of Cryptocurrency for Fundraising
- Year: 2019 - 2024
- Amount Raised: Approximately $41 million (Hamas) and $93 million (PIJ)
- Outcome: Seizure of cryptocurrency addresses and legal actions against facilitators
Case Summary: Since 2019, Hamas and other terrorist groups have solicited cryptocurrency donations through online platforms to evade financial sanctions and support activities in Gaza. The U.S. Department of Justice and Israeli authorities have seized related crypto addresses and prosecuted those involved. The U.S. Treasury has imposed sanctions and issued alerts to financial institutions to strengthen efforts against terrorist financing via cryptocurrency.
Tracking the Scam’s Unfolding:
Addresses related to this case include 0x21B8d56BDA776bbE68655A16895afd96F5534feD and 0x175d44451403Edf28469dF03A9280c1197ADb92c. These addresses can be tracked using advanced tools to uncover how cryptocurrency donations are channeled through various addresses and obscured.
Address Overview: 0x21B8d56BDA776bbE68655A16895afd96F5534feD
On the Ethereum Mainnet, this address has received a total of 5.88 ETH with 86 transactions and sent 5.71 ETH across 9 transactions. It currently holds a balance of 0.1355 ETH and 2,189.85 USDT.
Address Overview: 0x175d44451403Edf28469dF03A9280c1197ADb92c
On the Ethereum Mainnet, this address has received 1.08 ETH through 82 transactions and sent 1.07 ETH across 3 transactions. It currently holds a balance of 0.0094 ETH and 8,852.68 USDT.
For detailed analysis such as NFT holdings and DEX trades, you can explore further through Bitquery Explorer.
7. Synthetic Identity Fraud in Crypto Exchanges
Synthetic identity fraud involves using fake identities to bypass Know Your Customer (KYC) and Anti-Money Laundering (AML) controls on cryptocurrency exchanges. This technique allows individuals to evade detection and engage in illicit activities without proper vetting by the exchange’s compliance systems.
Incident Overview: BitMEX Case
- Year: 2021
- Fine: $100 million
- Outcome: BitMEX faced significant penalties for inadequate KYC/AML measures.
BitMEX Regulatory Actions: The CFTC fined BitMEX $100 million for inadequate KYC and AML controls, which allowed illicit trading and synthetic identity fraud. BitMEX has since enhanced its verification processes and restricted U.S. access to comply with regulations.
Tracking the Scam Unfolding:
Tracking synthetic identity fraud is challenging due to the use of fake identities to bypass KYC and AML controls. This complexity arises from the ability of fraudsters to obscure their true identities and create layers of fraudulent transactions across various addresses and blockchains.
Bitquery offers comprehensive solutions for this purpose. Its Coinpath API provides detailed tracking of fund flows across multiple addresses and blockchains, enabling the identification of suspicious patterns and connections linked to synthetic identities.
Additionally, real-time monitoring and the Cross-Chain Blockchain API enhance visibility across different platforms, improving the detection and investigation of synthetic identity fraud. These capabilities support robust KYC/AML procedures and fraud prevention efforts.
8. Laundering Illicit-Origin Privacy Coins
Laundering illicit funds with privacy coins involves using cryptocurrencies with strong anonymity features to hide the origin and movement of stolen funds. Privacy coins are designed to obscure transaction details, making it difficult for authorities to trace and investigate the source.
Incident Overview: Sanctioned Russian Cybercriminals
- Year: 2020
- Sanctions: U.S. Treasury Department sanctioned two Russian nationals
- Outcome: Millions in stolen virtual currency and U.S. dollars seized
Case Summary: Danil Potekhin and Dmitrii Karasavidi were sanctioned for a phishing scheme causing $16.8 million in losses. They used privacy coins to hide the stolen funds, complicating the investigation. Authorities traced the funds to Karasavidi’s account and seized millions in virtual and U.S. dollars.
Tacking the Scam Unfolding:
Addressing the challenge of tracking illicit funds through privacy coins is complex due to the inherent anonymity features of these cryptocurrencies. Privacy coins, like Monero, are designed to obscure transaction details, making it difficult for authorities to trace and investigate the source and movement of stolen funds.
In such cases, advanced tracking solutions are essential. Bitquery's services including Coinpath and its suite of APIs, provide investigators with the ability to analyze privacy coin transactions by identifying patterns, linking them to broader blockchain activities, and even tracing the flow of funds across different networks.
By offering visual insights and cross-chain monitoring, investigators can gain a comprehensive view of how illicit-origin privacy coins move through the system. These capabilities help uncover suspicious activity and support forensic analysis, making it easier to identify and mitigate illicit transactions even with privacy-enhanced cryptocurrencies.
9. Mixing Services and Privacy Wallets
Mixing services and privacy wallets obscure the origin and destination of cryptocurrency transactions by aggregating and redistributing funds across multiple addresses. This process, known as "mixing" or "tumbling," aims to break the link between the sender and receiver, making it difficult for authorities to trace the transaction flow.
Incident Overview: Helix Mixer and Coin Ninja
- Year: 2020
- Operation: Helix Mixer, operated by Larry Dean Harmon
- Amount Processed: Over $311 million
- Outcome: Harmon pleaded guilty, and forfeited over 4,400 Bitcoin
Case Summary: Larry Dean Harmon operated Helix Mixer from 2014 to 2017, laundering over 350,000 Bitcoin by partnering with darknet markets and making transactions untraceable. Arrested in February 2020 and pleading guilty in August, he agreed to forfeit over $200 million in assets and faces up to 20 years in prison.
Tracking the Scam Unfolding:
Tracking illicit funds through mixing services and private wallets can be challenging due to the deliberate efforts to hide the origins and destinations of transactions. These services aggregate and redistribute funds, breaking the link between the sender and receiver, and complicating investigations.
Bitquery’s Coinpoth streamlines this process by providing automatic address labeling and entity resolution, grouping related addresses into identifiable entities. This simplifies understanding of the connections between addresses involved in mixing activities, making the investigation more efficient. Additionally, transaction filtering and FATF (Financial Action Task Force) indicators assist in flagging suspicious activities, particularly those linked to money laundering.
For example, let’s analyze a prominent Ethereum address: 0x742d35Cc6634C0532925a3b844Bc454e4438f44e. This address is widely recognized for holding substantial Ethereum and has been involved in various high-profile transactions. Using Bitquery's wallet tracking features, you can:
- Wallet Transactions: Retrieve a comprehensive log of all transactions associated with the address.
- Holder Details: Identify the entities or individuals linked to the tokens held by the address.
- Inflow/Outflow: Track the movement of cryptocurrency in and out of the address.
- Balance: Display the current balance held by the address.
This address is used here as an example to demonstrate how Bitquery’s tools can aid in tracking and analyzing similar cases involving significant Ethereum transactions. Additionally, Crypto Travel Rule compliance ensures transparency and regulatory adherence by providing comprehensive tracking across transactions.
10. Fraudulent Cryptoasset Investment Platforms
Fraudulent cryptoasset investment platforms deceive investors by promising high returns on investments with little to no risk. These platforms often use deceptive tactics to attract and exploit investors, eventually collapsing and disappearing with the funds.
Incident Overview: PlusToken Scam
- Date: 2019
- Amount Raised: Over $2 billion
- Outcome: Ringleaders sentenced to up to 11 years in prison
Case Summary: Launched in 2018 by Chen Bo, PlusToken was a Ponzi scheme that promised high returns and attracted 2.7 million members. It used blockchain to appear legitimate but collapsed in 2019, leaving significant losses. Chinese authorities sentenced the ringleaders to up to 11 years in prison.
Fraudulent investment platforms like PlusToken often exploit investors by promising high returns with little risk, eventually disappearing with the funds. Read a detailed analysis on laundering through PlusToken here.
Address Overview: 0xecdbf2fec71ce3007b8fb7b5b46f946d60ba5a05
- Token: PlusToken (PLUS) on Binance Smart Chain
- Date Range: September 6, 2024 - September 13, 2024
- Total Transfers: 46,284
- Total Amount Transferred: 1,296,429,692.61 PLUS
This address was pivotal in the PlusToken scheme, handling a significant volume of token transfers.
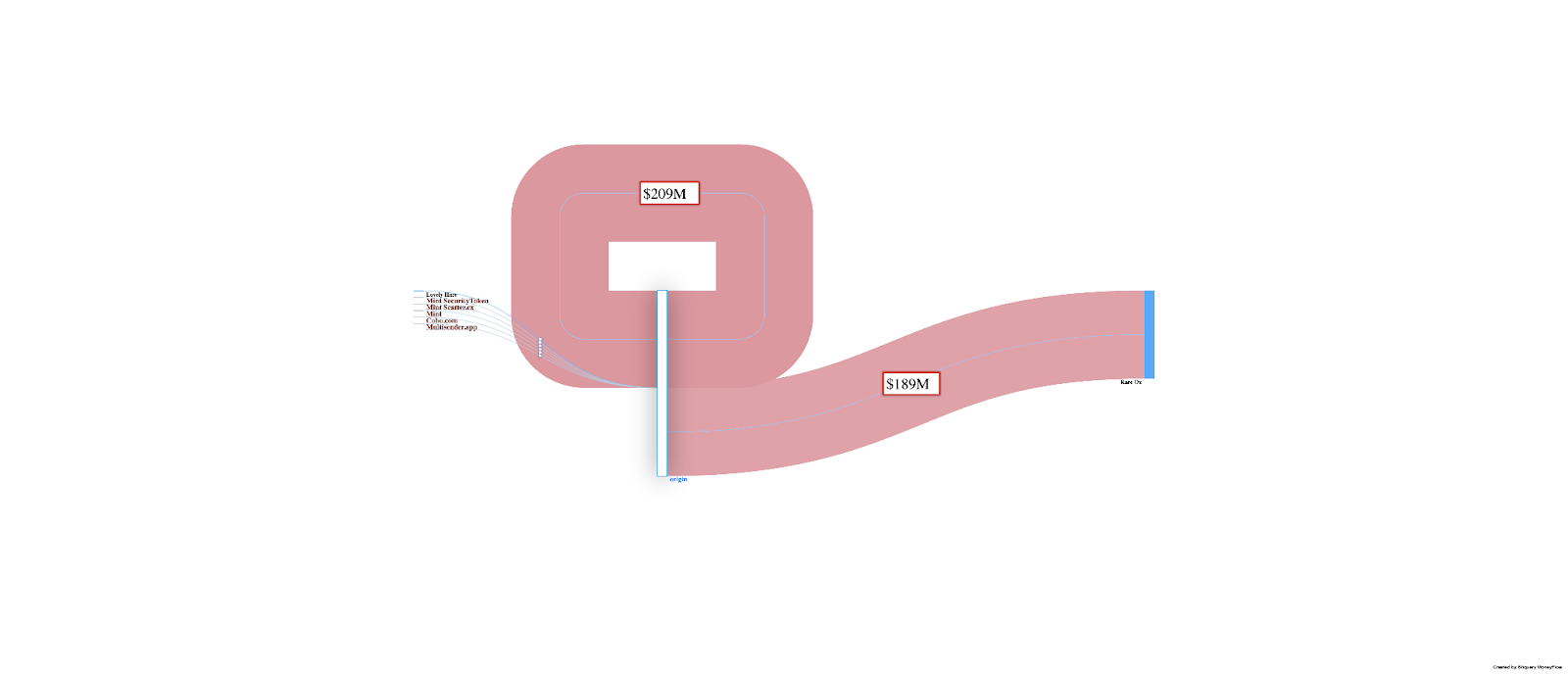
For a detailed analysis and insights into PlusToken transactions, including fund flows and address activities, explore the data on Bitquery’s Explorer here.
11. Chain Hopping
Chain hopping involves converting cryptocurrencies across different blockchains to obscure their origin and evade detection. This technique is used to launder money by creating complex transaction paths that make it difficult to trace the flow of funds.
Incident Overview: Lazarus Group's Cross-Chain Laundering
- Date: July 2022 - July 2023
- Amount Laundered: $900 million
- Affiliation: North Korean Lazarus Group
Case Summary: The Lazarus Group, a North Korean hacking organization, laundered about $900 million by using cross-chain bridges to convert cryptocurrencies across multiple blockchains rapidly. This "chain-hopping" technique made tracking the funds difficult and highlighted a shift from traditional laundering methods to more sophisticated techniques that obscure transaction trails.
Tracking Chain Hopping Activities
Chain hopping presents significant challenges in tracking and investigating illicit activities due to the rapid conversion of cryptocurrencies across multiple blockchains.
To address these challenges, Bitquery offers comprehensive tracking of transactions across various blockchains. It enables the visualization of fund movements by Moneyflow through cross-chain bridges and exchanges, making it easier to detect suspicious activities. Enhanced transparency through detailed mapping of transaction flows helps unravel obscured origins and destinations of funds. Analytical insights into transaction patterns provide a clearer understanding of how funds are transferred and laundered across different blockchains.
12. Tokens and Stablecoins
Tokens and stablecoins can be used to launder funds by disguising their origin through the use of digital assets that are often less scrutinized. This technique involves converting stolen or illicit funds into these assets, which can then be moved or exchanged with greater anonymity.
Incident Overview: BitMart Hack
- Date: December 4, 2021
- Amount Stolen: $200 million
- Assets Involved: Including SafeMoon
Case Summary: On December 4, 2021, BitMart was hacked, stealing $200 million in tokens, including SafeMoon, via a compromised hot wallet key. The stolen assets were laundered using tokens and stablecoins, making them hard to trace. The breach caused significant losses for users and highlighted risks in storing tokens on exchanges.
Tracking Tokens and Stablecoins
Tracking and recovering funds that have been laundered through tokens and stablecoins presents unique challenges. These digital assets often move through less scrutinized channels, and their transactions can be more difficult to trace due to their widespread use and the nature of their underlying technology. Identifying the movement of these assets and linking them back to illicit activities requires sophisticated tools and comprehensive analysis.
To address these challenges, Bitquery’s Coinpath provides crucial insights by tracing complex transaction paths across different blockchains including the movement of tokens and stablecoins. This tool visualizes the flow of assets and helps unravel the connections between different transactions and addresses even when funds are dispersed across multiple digital assets and exchanges.
The Token Holder API provides in-depth information about token holders and their transactions. For example, the SafeMoon token, with its address on the Binance Smart Chain (BSC) at 0x42981d0bfbaf196529376ee702f2a9eb9092fcb5, can be used to track transactions and holdings associated with this token. This API allows for tracking the flow of SafeMoon and other tokens involved in illicit activities, providing transparency and aiding in the recovery of stolen funds.
To illustrate how these can be applied, consider the SafeMoon token on the Binance Smart Chain with the address 0x42981d0bfbaf196529376ee702f2a9eb9092fcb5. Using Token Holder API, you can:
- Monitor Token Transactions: Get a comprehensive view of transactions involving SafeMoon.
- Analyze Holder Details: Understand who holds the tokens and their transaction patterns.
- Track Inflows/Outflows: See how much SafeMoon is coming in and going out of specific addresses.
- Check Balance: View the current balance of the token in various wallets.
These capabilities provide a clearer picture of the movement of illicitly obtained assets, helping to identify and recover stolen funds. For more detailed insights, explore the data on tracking platforms that offer these advanced features.
13. Use of Exchanges in High-Risk Jurisdictions
Exchanges based in jurisdictions with lax regulatory frameworks are often used to facilitate illicit activities, including money laundering and ransomware payments. These exchanges exploit weak regulatory oversight to conduct and conceal illegal transactions.
Incident Overview: BTC-e Exchange
- Date: Shut down in 2017
- Key Figure: Alexander Vinnik
- Amount Facilitated: Over $9 billion in transactions
Case Summary: BTC-e, run by Alexander Vinnik from 2011 to 2017, laundered over $9 billion and facilitated ransomware payments. The unregistered exchange lacked AML and KYC measures, attracting illicit activity. It was shut down in 2017, Vinnik was arrested and extradited, and he pleaded guilty to money laundering. The platform was linked to major hacks, including Mt. Gox.
Address Example for BTC-e Case
BTC-e Ethereum Wallet:
This address is associated with the BTC-e exchange, which facilitated over $9 billion in transactions and was involved in various illicit activities before being shut down in 2017.
Analysis Overview:
Using the provided address, we can analyze transaction data with the following statistics:
- Total Amount Sent: 8,091,160.88 ETH
- Total Amount Received: 8,091,210.24 ETH
- Number of Transactions Sent: 99,918
- Number of Transactions Received: 726,123
- Balance: 0.0002 ETH
- First Transaction Date: April 26, 2016
- Last Transaction Date: September 22, 2023
This data provides insights into the transaction history and balances of the address, showcasing the flow of funds and identifying patterns of activity.
To address the challenges of analyzing transactions involving high-risk exchanges like BTC-e, several tools can be invaluable.
14. Ransomware Payments
Ransomware attacks often use cryptocurrency to demand and receive payments, exploiting the anonymity of digital currencies. This method of payment helps attackers evade detection and facilitate their illicit gains.
Incident Overview: REvil Ransomware Attack
- Date: July 2021
- Amount Demanded: $70 million in Bitcoin
Case Summary: The REvil ransomware group targeted businesses worldwide, demanding $70 million in Bitcoin to restore encrypted files. Bitcoin’s pseudonymous nature helped the attackers hide their identities and transactions. The attack triggered an international law enforcement response aimed at tracking and recovering the ransom payments.
Challenges in Tracking Ransomware Payments
Ransomware attacks leverage the anonymity of cryptocurrencies to demand and receive payments, making it challenging to track and recover funds. The pseudonymous nature of Bitcoin, for example, complicates the identification of the attackers and their transactions, creating obstacles for law enforcement and investigators.
To tackle these challenges, advanced analytical tools can be highly effective. Coinpath enables the tracing of cryptocurrency transaction flows, helping to track ransomware payments across different addresses and exchanges. Sankey Diagrams and other visual tools assist in mapping out payment trails, identifying suspicious patterns, and understanding complex transaction flows.
Address and Transaction Monitoring features allow for continuous surveillance of specific addresses linked to ransomware activities. Additionally, the Auto Trace function in Moneyflow simplifies tracking by automatically following the trail of funds and uncovering connections. These capabilities collectively enhance the ability to analyze, track, and potentially recover ransomware payments.
15. Peer-to-Peer Platforms
Illicit activities can also occur on peer-to-peer (P2P) trading platforms, where individuals trade directly with each other rather than through centralized exchanges. These platforms can be exploited for fraud and scams, often involving deceptive promises and fraudulent schemes.
Incident Overview: My Big Coin Scam
- Date: 2018
- Amount Defrauded: $6 million
- Key Figure: Randall Crater
Case summary: My Big Coin, a fraudulent P2P platform, promised high returns from a non-existent cryptocurrency, defrauding investors of $6 million. Founder Randall Crater was convicted of wire fraud and sentenced to over eight years in prison, with nearly $7.7 million forfeited. His false claims of gold backing and major financial partnerships led to significant losses and set a regulatory precedent in the U.S.
Tracking the Fraud on Peer-to-peer Platforms
P2p platforms are susceptible to fraud due to their decentralized nature. These platforms often lack centralized oversight, making them ripe for deceptive schemes. Bitquery addresses these challenges effectively: Coinpath monitors transactions to uncover suspicious activities, Address Analysis reveals connections to fraudulent schemes, Fraud Detection identifies unusual transaction patterns, and Auto Trace continuously tracks transactions, aiding in the detection and investigation of P2P-related fraud.
16. Fake ICOs and Token Sales
Fraudulent Initial Coin Offerings (ICOs) and token sales are a significant threat in the cryptocurrency space. Scammers use these methods to deceive investors with promises of high returns or innovative technologies that don't exist.
Incident Overview: Centra Tech ICO Scam
- Date: 2017
- Amount Defrauded: $25 million
- Key Figures: Robert Farkas, Sohrab Sharma, Raymond Trapani
- Celebrity Endorsements: Floyd Mayweather, DJ Khaled
Case Summary: Centra Tech’s ICO falsely promised a multi-blockchain debit card and claimed partnerships with Visa and Mastercard, raising over $25 million before being exposed. Co-founder Robert Farkas pleaded guilty to securities and wire fraud, facing up to 87 months in prison.
Detecting Fraudulent ICOs and Token Sales
Fraudulent ICOs and token sales exploit investors with false promises and celebrity endorsements. These challenges are through Bitquery’s Moneyflow. It tracks fund flows from investors to issuers, ensuring transparency in ICO fund use and token issuance; Token Holder API provides detailed data on token distribution and wealth metrics; and Auto Trace follows funds from specific ICO addresses. Additionally, FATF-based filtering helps detect suspicious activities and potential money laundering, enhancing the ability to identify and investigate fraudulent schemes.
17. Money Mules or Fraudulent Documents at Legitimate Exchanges
Using money mules or fake documents to conduct transactions at legitimate exchanges is a tactic employed to launder money or evade regulatory scrutiny. This method involves leveraging trusted platforms to conceal the illicit nature of funds by using falsified identities or fraudulent documents.
Incident Overview: WEX Exchange Money Mule Operation
- Date: 2017–2018
- Exchange: WEX (formerly BTC-e)
- Key Issues: Fake registration details, use of money mules
Case Overview: WEX, which took over from BTC-e after its shutdown in 2017 due to a $4 billion fraud case, continued operating under problematic conditions. The exchange faced regulatory issues for using fake identities and documents, leading to the suspension of domains like wex.nz by the New Zealand Domain Name Commission.
This suspension caused significant losses for users who were redirected to mirror domains like wex.link. The DNC’s actions were part of a broader effort to enforce data validation and secure domain spaces, with victims advised to report issues to law enforcement and Netsafe.
18. Crypto-Enabled Trafficking and Smuggling
Using cryptocurrencies to facilitate trafficking and smuggling operations involves leveraging digital currencies to conduct illegal activities, taking advantage of their anonymity and global reach.
Incident Overview: Silk Road Marketplace and James Zhong's Bitcoin Theft
Date: Silk Road (2011-2013); James Zhong's theft (September 2012); Zhong’s guilty plea (November 2022).
- Marketplace: Silk Road (dark web marketplace)
- Key Issues: Cryptocurrency theft, dark web operations
Case Summary: Silk Road, a dark web marketplace, was shut down in 2013, and its founder Ross Ulbricht was sentenced in 2015. James Zhong stole 50,000 Bitcoin from the platform in 2012, hiding the funds, which were worth over $3.36 billion when seized. The case highlighted both vulnerabilities in dark web markets and the effectiveness of advanced tracking.
Address Analysis
The Bitcoin address 1HQ3Go3ggs8pFnXuHVHRytPCq5fGG8Hbhx, potentially related to the Silk Road case, recently exhibited significant activity. From September 6, 2024, to September 13, 2024, the address showed 955 outputs with a balance of 0.00757271 BTC. The latest inbound transfers included small, frequent transactions, with a total volume of 0.007 BTC over the period. This pattern of frequent small transactions and the relatively unchanged balance suggest careful management or movement of funds, indicative of ongoing monitoring or concealment efforts related to illicit activities.
19. Social Engineering Scams
Scammers use deceptive tactics to manipulate individuals into giving away their crypto assets or personal information through personal connections and fabricated investment opportunities.
Incident Overview: $4 Million Gone in Seconds
- Date: August 7, 2024
- Amount Lost: $4 million USD
- Key Issues: Ponzi scheme, social engineering, fake investment opportunities
Case Summary: Victims were deceived on social media by individuals posing as trustworthy figures, who used small withdrawals to build trust before promoting a Ponzi scheme with promises of high returns. The scam employed buzzwords like "arbitrage" and "smart contracts" to manipulate victims into larger investments. Two major victims lost $4 million and USD 3 million, leading to significant financial losses and emotional distress.
In this specific case, the victims used Strike to convert fiat into Bitcoin.
Bybit Wallet: 1FeM5NFwxpsDegpxfvMw2u18WsEikcbk3C
-
Binance Hot Wallets:
The trace revealed that the funds were deposited into these known exchange wallets. Due to the centralized nature of these services, further investigation often involves liaising with the exchanges to determine the subsequent handling of these assets.
20. Individuals or Small Cells
Small groups or individuals engaging in crypto crimes can orchestrate large-scale frauds with sophisticated schemes and manipulative tactics.
Incident Overview: OneCoin Fraud
- Date: 2014–2017
- Amount Defrauded: Over $4 billion
- Key Figure: Ruja Ignatova
Case Summary: Ruja Ignatova, the "Cryptoqueen," launched OneCoin in 2014, claiming it as a revolutionary cryptocurrency and attracting many investors. However, OneCoin was exposed as a pyramid scheme, deceiving investors and defrauding millions of dollars. The scam caused over $4 billion in losses, and Ignatova fled after being charged with fraud and money laundering, disappearing while on the FBI's Most Wanted list.
Conclusion
Understanding various crypto crime typologies is crucial as criminal tactics evolve with cryptocurrency technology. Awareness of these methods helps in implementing effective strategies to protect assets and prevent financial losses.
Advanced tools like Bitquery’s MoneyFlow are essential for tracking and tracing cryptocurrency transactions, offering precise detection of suspicious activities. These tools enhance your ability to safeguard investments and recover lost assets by providing detailed insights into transaction flows and potential fraud.
—
Written by Aakash
Subscribe to our newsletter
Subscribe and never miss any updates related to our APIs, new developments & latest news etc. Our newsletter is sent once a week on Monday.


