Understanding Different MEV Attacks: Frontrunning, Backrunning and other attacks
MEV, also known as maximal extractable value or miner extractable value during Ethereum's Proof-of-Work era, has captured the attention of many, from MEV researchers to core developers. Opinions about MEV vary, with some viewing it positively and others negatively. Regardless of personal opinions, the reality is that MEV is a lasting aspect, at least for the foreseeable future. Let's explore how MEV researchers can extract more value from the network using different methods.
MEV, or maximal extractable value, refers to the maximum value that can be extracted from a proposed block by arranging and sequencing transactions. Those proposing the block have full control over the transactions included and their order. To maximize the additional value within a block, these proposers strategically place their own transactions to enhance their profitability.
Front Running Attack
A front-running attack occurs when transactions are rearranged, placing the attacker's transaction before the target transaction. This attack can be utilized to extract profits or execute smart contract calls to accomplish specific objectives.
The malicious actor intentionally assigns a higher gas price to their transaction, effectively offering a form of incentive to miners. This higher gas fee is aimed at persuading miners to prioritize their transaction over the original one in a block. Despite the drawback of reducing the attacker's profit margin, this higher gas price is a crucial aspect of the front-running strategy. It elevates the likelihood that their transaction will be processed before the original, ensuring the success of the front-running attack.
Back Running Attack
Backrunning is a technique where an attacker places their malicious transaction after the victim transaction gets executed. An attacker can accomplish this by lowering the gas price of the malicious transaction. This will make sure that the victim transaction is prioritized over the backrun transaction. Real example is explained in the Sandwich Attack section.
Sandwich Attack
When an individual identifies a favorable situation to sandwich a transaction, they execute a trade ahead of the transaction (referred to as "frontrunning") and subsequently follow it with a trade after the transaction (referred to as "backrunning"). This strategy is employed to influence the price of the trade.
Due to the inherent structure of Automated Market Makers (AMM) like Uniswap, these executed trades are tactically designed to manipulate the asset prices, creating a potential avenue for financial gains.
Instances of these extractions commonly occur when users engage in swaps on decentralized exchanges (DEX). DEXs operate using automated market makers employing specific formulas to establish token prices in relation to others. This computational process relies on the token supply within a liquidity pool, providing an opportunity for MEV bots to derive significant value from specific trades.
Consider a scenario where an individual named Alex is executing a transaction to purchase 15 ETH with 40k USDT on a DEX, at a rate of 2.7k USDT per ETH. Given the substantial size of the transaction, Alex anticipates encountering an elevated level of price slippage, creating a vulnerability for a potential sandwich attack.
An observer, named Eve, operates an MEV bot and detects this transaction in the mempool. Eve strategically initiates two transactions, preceding and following Alex's trade. In the first transaction, Eve acquires a substantial amount of ETH, causing an upward shift in the price due to the AMM's valuation formula. It's noteworthy that the adjusted price remains within the slippage range accepted by Alex. Following this, the third transaction involves the MEV bot selling the recently acquired ETH to Alex for USDT at an increased price, resulting in a profit for the bot.
Arbitrage
Decentralized exchanges may list different prices for the same tokens due to different levels of demand. A wide price discrepancy may be an opportunity for MEV extraction. Bots can exploit these situations by buying tokens at a lower price at one exchange, turning around, and selling them on a second exchange at a higher rate. For ex. checkout this transaction
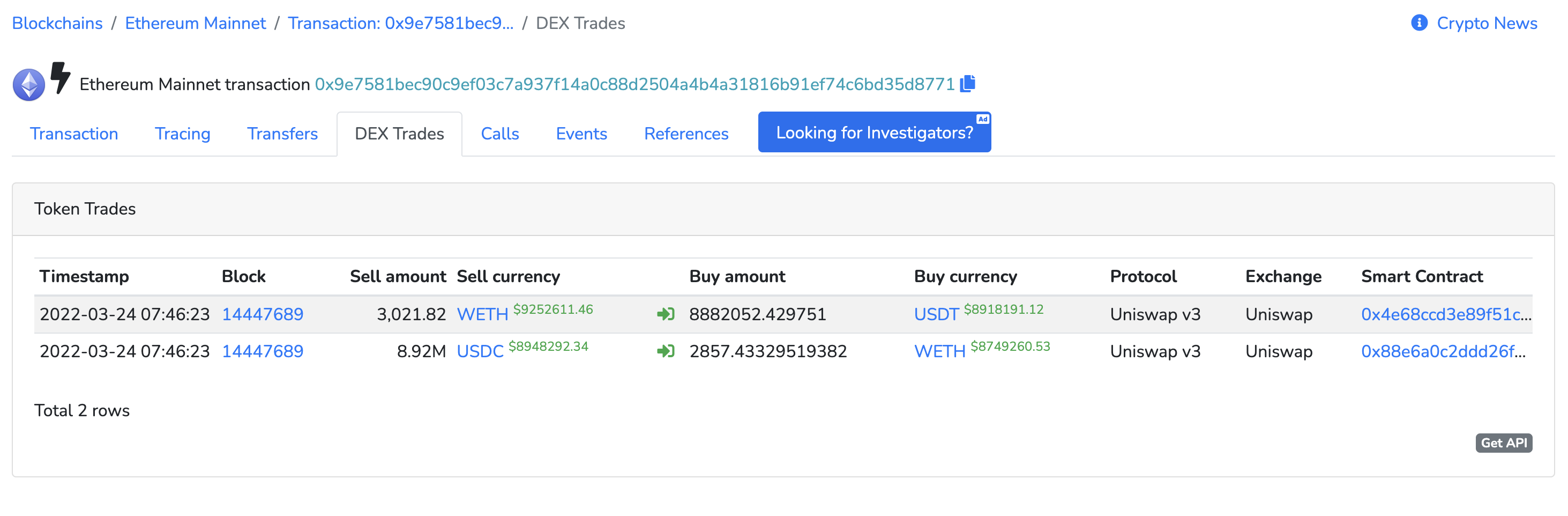
In this transaction, 2,857.4332 ETH was sold with 8,920,620.009 USDC. The same USDC Is traded on different platforms and converted to 8,882,052.429751 USDT because of the Arbitrage Opportunity. Finally it is converted back to 3,021.8233352922498 ETH. Overall an MEV bot made 147 ETH in profit.
Liquidation
In a DeFi lending space, users must deposit crypto to be used as collateral. If a user isn’t able to repay their loans, the protocols often allow other participants the chance to liquidate the collateral and gain a liquidation fee from the borrower. Those searching for MEV opportunities may compete to find borrowers primed for liquidation so that they can gain the liquidation fee for themselves.
After taking a long position on ETH, a user was unable to maintain their position when the price of ETH suddenly dropped, which caused the user's position to become liquidatable. The resulting liquidation process was carried out by a liquidator who repaid 218k USDC on behalf of the user. In return, the liquidator received 88k cETH worth of collateral as a reward.
Time bandit attack
Time bandit attacks is a MEV strategy involving the reorganization of past blocks. If the reward is great enough, Ethereum miners may be incentivized to propose competing blocks containing altered transactions at the expense of users and other network stakeholders.
To put it simply, a time bandit attack is the same as a 51% attack in terms of the goal they want to achieve. Both attacks want to rewrite Ethereum history and reverse transactions on the blockchain.
The difference is, with a 51% you need 51% of the miner's hashpower under your control to execute. This time bandit proposal put forward by a few people that wants to make this auctionable in the free market. For example, if you found very lucrative MEW opportunities in the last blocks, you can propose to rewrite ethereums history and remine these blocks to make a profit of the opportunity you found in the past. So to rewrite history. You offer a reward for the miner that executes this attack to incentivize them to do so.
It's a mechanism to put the consensus of the current state of the chain up for auction to the highest bidder. Instead of controlling 51% and performing this attack, anyone can put up a proposal to rewrite the history and offer a reward to miners for doing so. Putting the integrity of the Ethereum network at risk for a few extra bucks.
Uncle bandit attack
In the Ethereum blockchain, users sometimes group transactions into bundles and submit them together. These bundles are expected to be included in the blockchain entirely or not at all. However, occasionally two blocks are mined almost simultaneously, and only one of them is added to the blockchain. The other block becomes an "uncle" or orphaned block.
Let's consider a case where a user named Robert noticed that a specific bundle, known as a "Sandwich" bundle, was included in an uncle block. An attacker took advantage of this situation by grabbing only the "Buy" part of the Sandwich bundle from the uncle block, discarding the rest, and then adding an arbitrage transaction after the Buy. The attacker then submitted this altered bundle as a new transaction, and it was successfully mined. This type of attack is referred to as an "uncle bandit attack." Unlike a time-bandit attack, where an attacker exploits delayed information, an uncle bandit attack involves seizing an opportunity found in an uncle block and bringing it forward. It emphasizes that attacks on the Ethereum blockchain can extend beyond the mempool (where pending transactions wait to be confirmed) into uncle blocks as well.
Bitquery Mempool API
The Mempool API allows you to access real-time data from the mempool for Ethereum. You can use this API to monitor transactions, token trades, transfers, and any data stored in the mempool.
By analyzing Mempool data, researchers can gain insights into transaction behaviors, identify potential arbitrage opportunities, and study the patterns of transaction inclusion in blocks. This information is crucial for understanding and mitigating the impact of MEV-related activities on decentralized networks, as it allows researchers to observe transaction order, prioritize, and execution dynamics, helping to develop strategies and solutions to address these challenges.
About Bitquery
Bitquery is a set of software tools that parse, index, access, search, and use information across blockchain networks in a unified way. Our products are:
- Coinpath® APIs provide blockchain money flow analysis for more than 24 blockchains. With Coinpath’s APIs, you can monitor blockchain transactions, investigate crypto crimes such as bitcoin money laundering, and create crypto forensics tools. Read this to get started with Coinpath®.
- Digital Assets API provides index information related to all major cryptocurrencies, coins, and tokens.
- DEX API provides real-time deposits and transactions, trades, and other related data on different DEX protocols like Uniswap, Kyber Network, Airswap, Matching Network, etc.
If you have any questions about our products, ask them on our Telegram channel. Also, subscribe to our newsletter below, we will keep you updated with the latest in the cryptocurrency world.
Subscribe to our newsletter
Subscribe and never miss any updates related to our APIs, new developments & latest news etc. Our newsletter is sent once a week on Monday.


