
How Upbit hackers laundered millions using crypto exchanges?
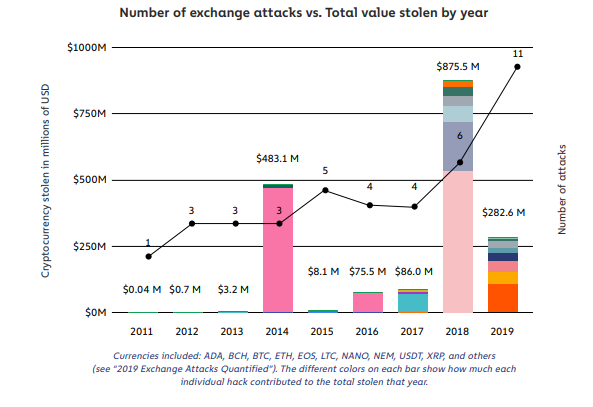
In 2019, hackers stole $283 million worth of cryptocurrencies in 11 hacks. Among these hacks, hackers also successfully targeted the Upbit exchange. In this article, we will investigate the Upbit hack and follow the stolen cryptocurrencies, using Coinpath® APIs.
What is Coinpath®?
Coinpath® APIs provide blockchain money flow analysis for more than 24 blockchains. With Coinpath’s APIs, you can monitor blockchain transactions, investigate crypto crimes such as bitcoin money laundering, and create crypto forensics tools. Read this to get started with Coinpath®.
Looking for end to end Crypto investigation tool? Explore Coinpath Moneyflow, built for investors and law enforcement agencies. Check it out here!
The Upbit Hack
On November 27, 2019, at 1:06 PM, Upbit, a Korean cryptocurrency exchange, observed a large transaction that went out from the exchange wallet. The next day, Upbit’s team notified that there was a security breach, and hackers stole 342K ETH (approx. $48.1 million) and transferred funds to this address.
In this article, we will investigate Upbit’s stolen money by following the transactions created by hackers in subsequent days and months.
Tracking money outflow
Criminals often use multiple intermediate wallets and other services to launder stolen cryptocurrencies. In other words, they create layers of transactions to make tracing difficult before converting funds into fiat or other cryptocurrencies. This process is called layering, in which every layer represents a segment.
A hop is referred to the number of segments(groups of wallets) that funds move through from its source to its destination.
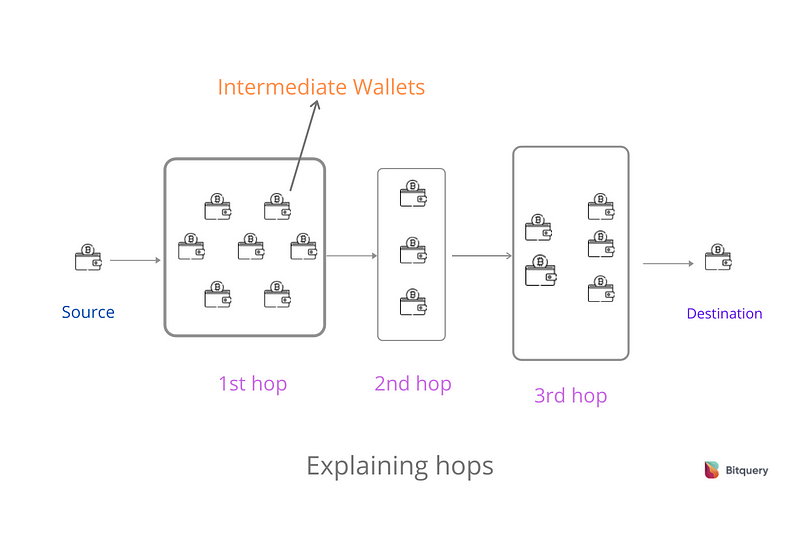
Hops explained
Coinpath® technology helps in tracking funds over multiple hops to discover the source or destination of the money.
Now, let’s track money outflow for Upbit’s hackers’ address over five hops. As you can see in the image below, hackers transferred large amounts of ETH to unknown addresses. If you noticed, many addresses received a similar amount of ETH(Ex- 5000 ETH) through multiple transactions, over 3–5 hops. Most probably, these addresses belong to hackers.
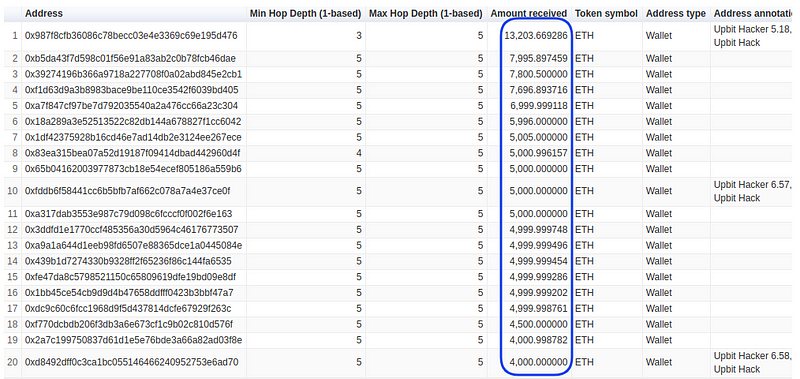
Upbit hackers money outflow over 5 hops
Let’s dig deeper by increasing hops to 10. Note, in the backend, Coinpath® is processing thousands of transactions to provide these results.
As you can see, over 10 hops, some known exchanges started to appear. For example, one of the Binance exchange wallets received 59,833 ETH through multiple transactions, over 10 hops.
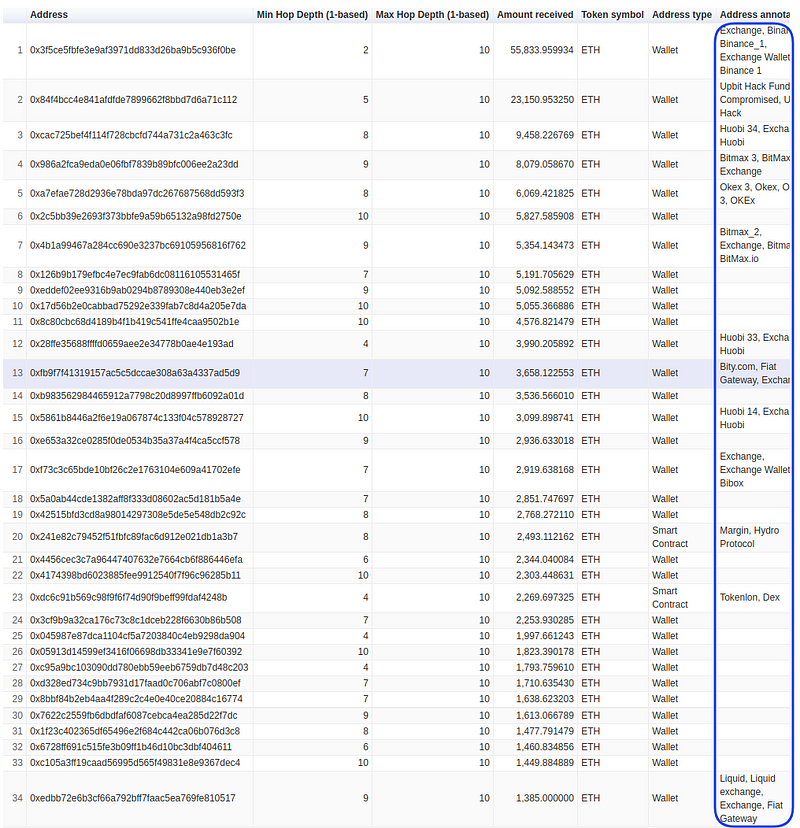
Upbit hackers money outflow over 10 hops
Tracking funds using Coinpath®
Coinpath® also provide a Paths API using which you can get all the intermediate transactions from a source to destination. For example, let’s see how hackers transferred stolen funds to Bity.com.

Bity received 541 ETH from hackers
As you can see, Bity.com, a crypto exchange service, received 541 ETH over 7 hops from hackers’ addresses. However, hackers created multiple intermediate wallets and distributed the funds to make them untraceable.
Upbit hackers’ initial wallet → 6 intermediate wallets →Bity’s wallet (7th hop)
With Path’s API data, we have created the following image to visualize how funds moved through intermediate wallets before reaching Bity.com.
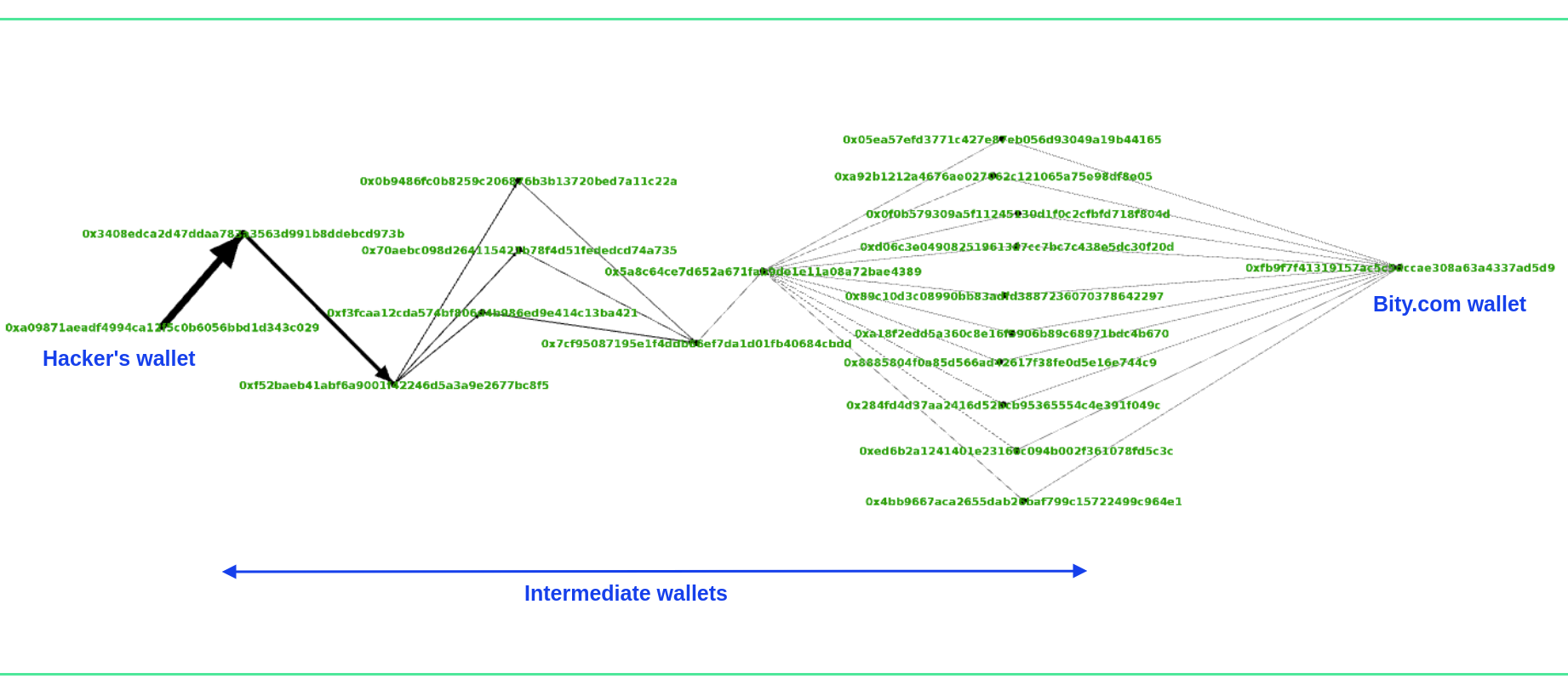
Graph view of hackers laundering funds to Bity.com (created using Gephi)
In addition, we can also get the transactions that hackers sent to bity.com. Notice, date, and the amount of the transactions. All transactions were sent to Bity within 45 minutes and they all are around 60 ETH.
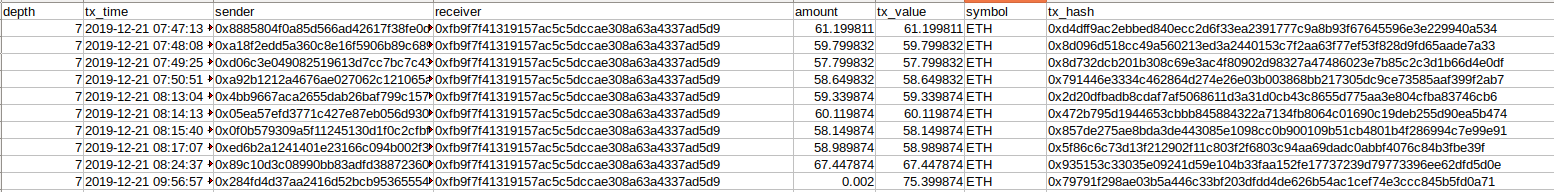
Transactions received by Bity from upbit hackers’ address
Majority of Upbit funds end up on Exchanges
However, when we checked for 12 hops, we found that hackers sent 3,661 ETH to Bity. Besides, hackers also sent the majority of the funds on prominent crypto exchanges.
As you can notice in the following image, hackers sent more than 100K ETH to Binance. Besides, they sent money to exchanges like Huobi, Bitmex, Kraken, and Liquid exchange (Check attached data).
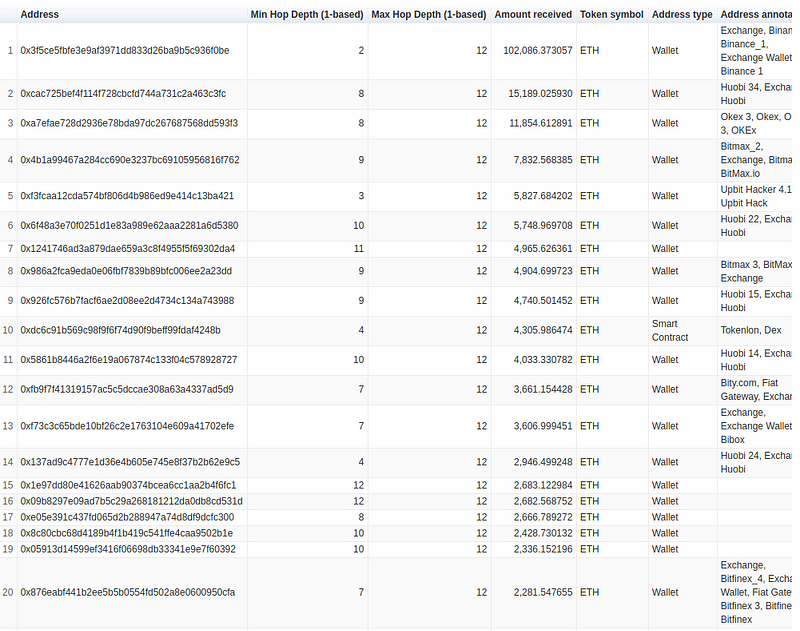
Upbit hackers money flow over 12 hops (Top 20 results)
Investigating crypto crimes using Coinpath® APIs
We don’t know how much funds Upbit had recovered. However, a significant amount of funds could have been retrieved by real-time monitoring of stolen cryptocurrencies. Exchanges like Binance and Bitmex can freeze funds as soon as they receive a transaction from a suspected wallet.
Using Coinpath® APIs you can stop cryptocurrency money laundering in real-time. Learn more about the Coinpath use cases here.
About Coinpath®
Coinpath® APIs provide blockchain money flow analysis for more than 24 blockchains. With Coinpath’s APIs, you can monitor blockchain transactions, investigate crypto crimes such as bitcoin money laundering, and create crypto forensics tools.
If you have any questions about Coinpath®, ask them on our Telegram channel. Also, subscribe to our newsletter below, we will keep you updated with the latest in the cryptocurrency world.
Coinpath® is a Bitquery product. Bitquery is a set of tools that parse, index, access, search, and use information across blockchain networks in a unified way.
Also Read
Subscribe to our newsletter
Subscribe and never miss any updates related to our APIs, new developments & latest news etc. Our newsletter is sent once a week on Monday.


