Attacker Stole 807K ETC in Ethereum Classic 51% Attack
In the last article, Ethereum Classic 51% Chain Attack Jul 31 2020, we have described the facts related to Ethereum classic attack, which took place between Jul 31 and Aug 1. In this article, we have analyzed the transactions during the attack in both forks of the chain.
Key Takeaway: Attacker double-spent 807,260 ETC ($5.6 million) during this attack and spent 17.5 BTC ($192K) to acquire the hash power for the attack. The attacker also got 13K ETC as a block mining reward, which we are not including in our double-spent calculation.
Data collection from reorged and non-reorged chain
We at Bitquery collected data from the Ethereum Classic node based on Open Ethereum software. As it appeared after the fork, this software had a bug that prevented chain-reorg past a certain block number. As a result, we had all data preserved, including a series of blocks that were mined by other miners on Open Ethereum software after the reorg happened.
It appeared that the only way to catch up with the reorged chain is to move to other node software, and we selected Geth. But before doing that, we stored all the data of the non-reorged chain, in a separate database for future analysis.
After the Geth node synced and we re-indexed the data starting from the block 10904146, where reorg started.
As a result, we now have two datasets, that we exposed in Bitquery explorer interface and GraphQL API:
- Non-reorged chain, from Open Ethereum node (On which every miner worked)
- Reorg’d chain from Geth node (On which attacked worked)
These datasets have precisely the same data until the block 10904146, and the difference starts from the next block. For example, compare the next block, 10904147:
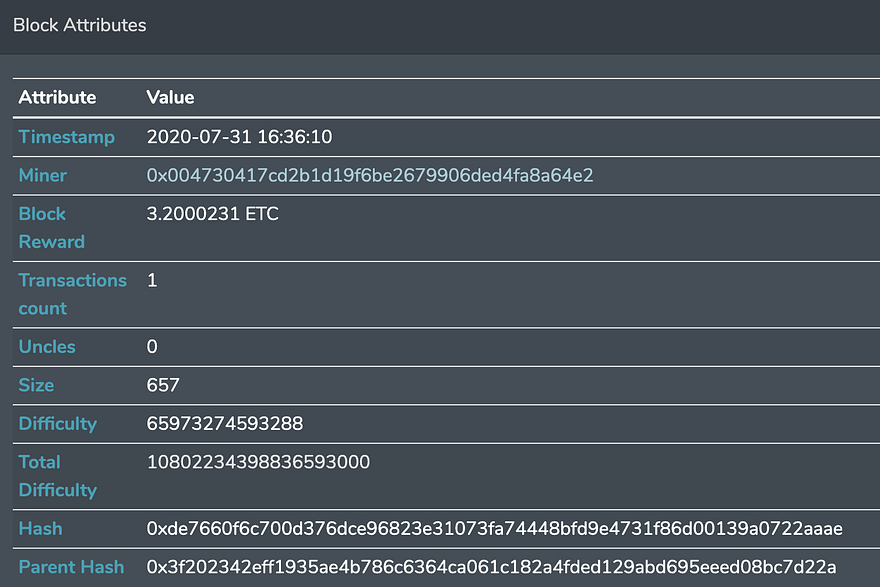
10904147 for non-reorged chain
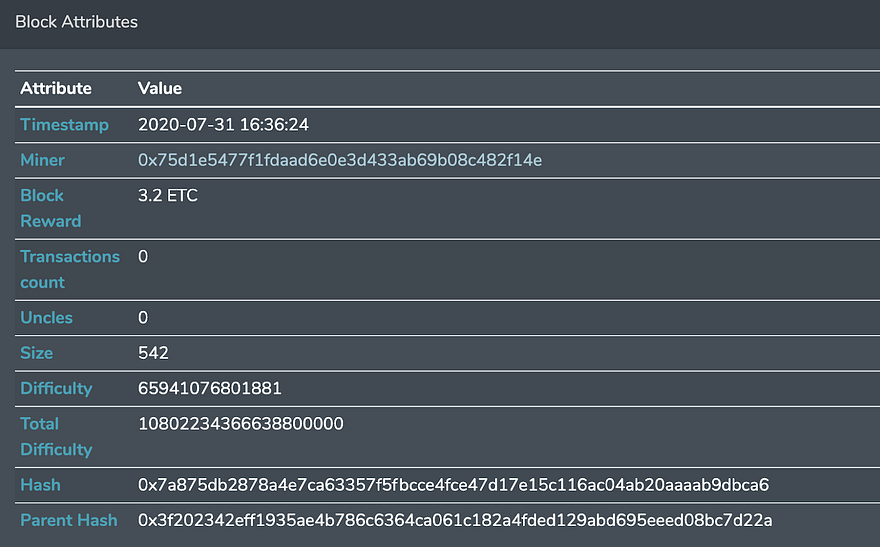
10904147 for reorged chain
In general, you can use the URLs in the form:
https://explorer.bitquery.io/ethclassic to query reorged chain ( currently accepted chain, and the chain with attacker’s mined blocks )
https://explorer.bitquery.io/ethclassic_reorg to query non-reorged chain (Chain with blocks which are discarded)
There are a couple of differences in these blocks in the chain:
- Height is the same, but hashes are different, as these blocks have different content.
- The parent hashes are the same, as they were pointing to the same original block, from which the fork started (10904146)
- Miners are different. Miner for the reorg’ed chain is the attacker 0x75d1e5477f1fdaad6e0e3d433ab69b08c482f14e , who mined more than 3500 blocks during 12 hours to execute the reorg. Miners for the non-reorged chain are some regular miners, who continued to mine the blocks, not knowing about the attacker.
- Not just blocks, but transactions, transfers, smart contract calls, and events are different in the reorged and non-reorged chain.
Let’s have a look at the attacker’s mining activities.
Attacker’s mining activity
The Attacker managed to insert blocks from the block height from 10904147 to 10907761. After the block 10907761, he continued to mine some blocks, but that did not cause major reorgs. The attacker’s activity can be seen at:
In total, the attacker mined 4280 blocks for four days. Note that he did only a little mining before and stopped mining after the attack. This is not the behavior of a regular miner.
In result, the miner sent all the mining reward money (13K ETC ) to address 0x401810b54720faad2394fbe817dcdeae014066a1, where it resides at the time of writing:
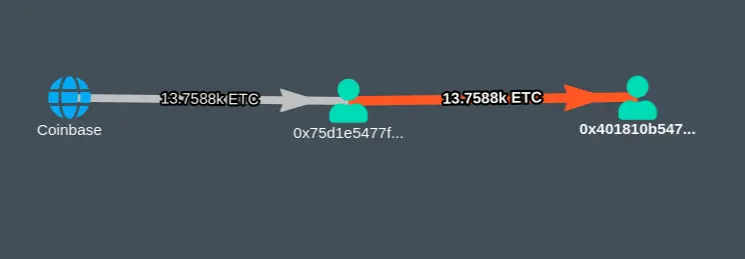
attacker’s mining reward transactions
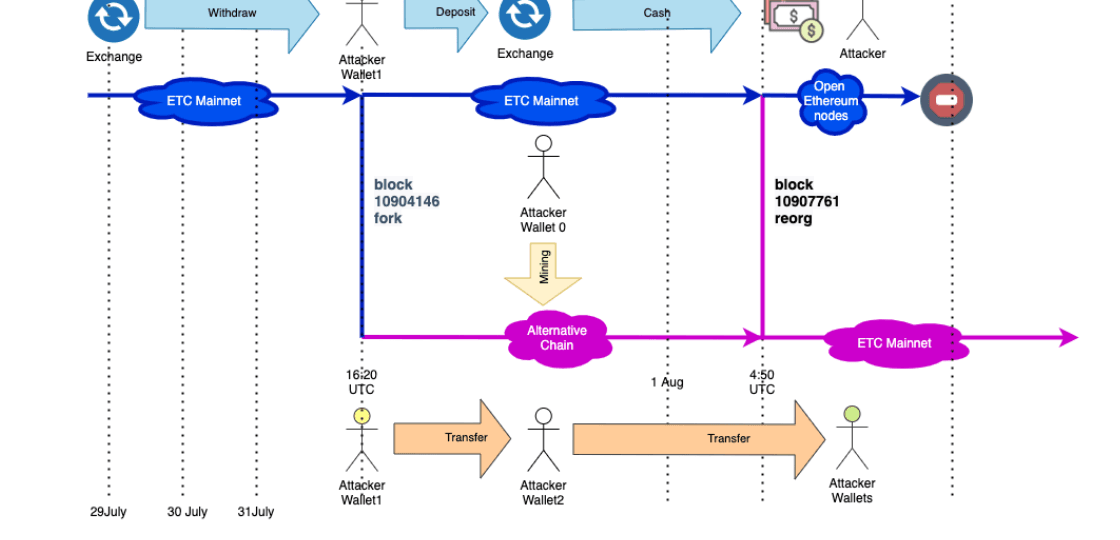
Attack Timeline
Based on our investigation, the attacker performed the following action to execute the 51% attack:
- July 29–31. The attacker withdraws 807K ETC from a Crypto exchange to several wallets.
- Jul 31, 16:36 UTC. The attacker started mining blocks by purchasing the hash power for double price from Nicehash provider daggerhashimoto, as we found in the first article. The total cost of mining is approx 17.5 BTC ( ~$192,000 )
- Jul 31, 17:00–17:40 UTC. The attacker created private transactions, sending money to his/her own wallets, and inserted these transactions in the blocks he/she was mining. No one saw these transactions because the attacker didn’t publish the blocks.
- Jul 31, 18:00– Aug 1, 2:50 UTC. The attacker sends money back to the Crypto exchange using intermediary wallets on the non-reorged chain, which was visible to everyone. During this, the attacker has plenty of time to monetize this money — convert to USD and withdraw or change them to BTC, whatever. Long attack duration(12 hours) allowed attackers to split operations into smaller parts to avoid any suspicion.
- Aug 1, 4:53 UTC, the attacker publishes his/her blocks with the version of the transaction created in step #3 and executed the chain re-organization. It means that transactions on step #4 replaced with transactions on step #3.
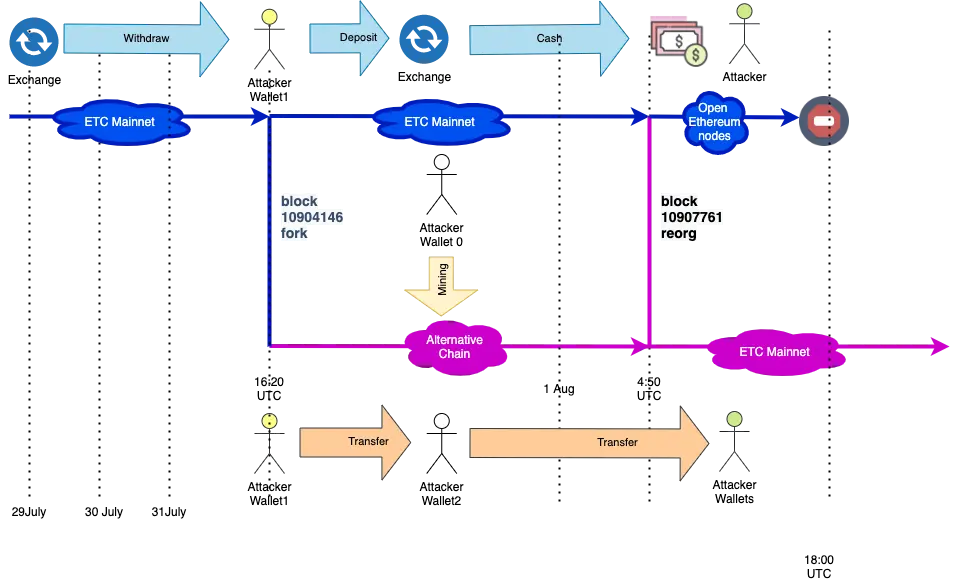
Now let’s see a detailed look at the steps and how miner was able to get away with more than ~807K ETC ($5.6 million).
Transactions inserted by the attacker ( in reorged chain )
There are just 11 transactions, that miner inserted during the attack. This fact probably caused the speculations that “The offending miner has lost access to internet access for a while when mining.” Noteworthy, that these transactions were not sent to other miner’s transaction memory pool (mempool). So they are not mined by other miners in the network.
Take a look at these transactions:
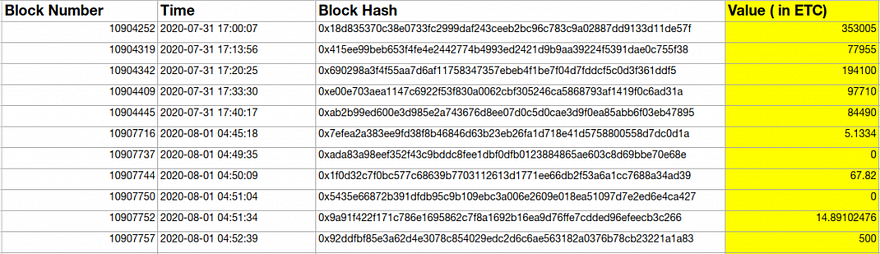
Notice, first five transactions with high amounts of ETC value. Let’s check these transactions one by one.
First Transaction (Value — 353005 ETC) (Tx)
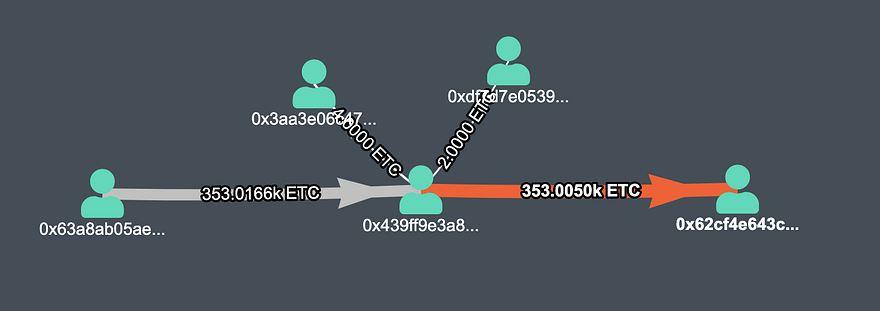
The first transaction mined by attacker 353K ETC
Second Transaction (Value — 77955 ETC) (TX)
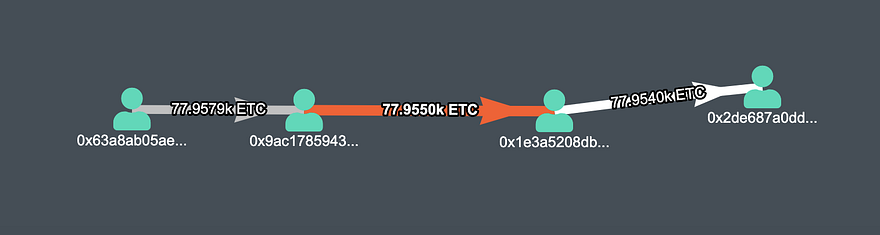
The second transaction mined by attacker 77.955K ETC
Third Transaction (Value — 194100 ETC) (TX)
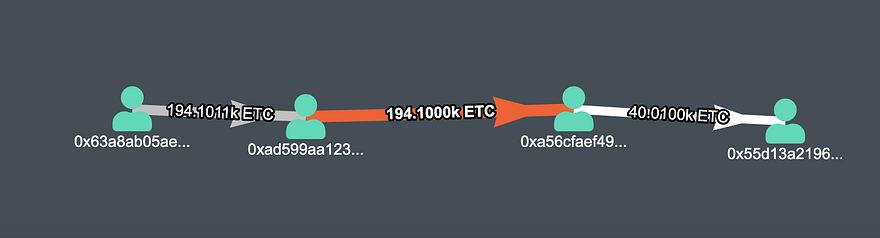
Third transaction mined by the attacker, value — 194.1K ETC
Fourth Transaction (Value — 97710 ETC) (TX)
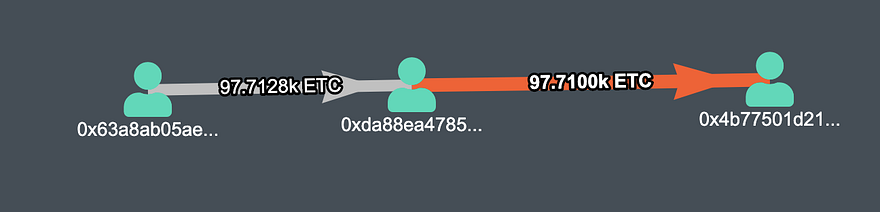
Fourth Transaction mined by the attacker, value — 97.1 ETC
Fifth Transaction (Value — 84490 ETC) (TX)
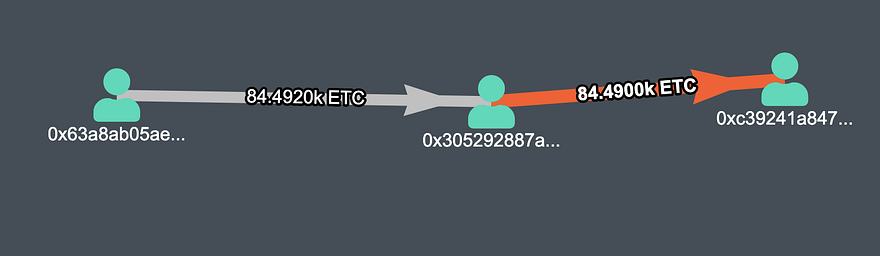
fifth transaction mined by the attacker, value — 84.49 ETC
Comparing these transactions, you will notice the pattern:
- Amounts are in thousands of ETC
- All the Transaction originated from the address 0x63a8ab05ae4a3bed92580e05e7dce3b268b54a7f
- All the transactions happen within a 40 minutes time range starting from 17:00 July, 31, just before the attack began.
Wallets are ready to execute the 51% attack
To perform a 51% attack, the attacker had to own the money in wallets he/she controls. There are 5 addresses, that had prepared balances before the attack:
- 0x439ff9e3a81a4847d0c2041c06e5a272883f69f2, received 353K ETC from 0x63a8ab05ae4a3bed92580e05e7dce3b268b54a7f in 22 transactions at 29–30 July, 2020
- 0x9ac1785943ead4dafb2198003786b4b29143f081, received 78K ETC from 0x63a8ab05ae4a3bed92580e05e7dce3b268b54a7f in 7 transactions at 30–31 July, 2020
- 0xad599aa123c2b5b00773b9bfadacf8c3e97ea72d, received 194K ETC from 0x63a8ab05ae4a3bed92580e05e7dce3b268b54a7f in 16 transactions at 30–31 July, 2020
- 0xda88ea478545581eafffa3598fd11fc38f13c508, received 97.7K ETC from 0x63a8ab05ae4a3bed92580e05e7dce3b268b54a7f in 7 transactions at 30–31 July, 2020
- 0x305292887ad1ffa867e8564c804575f3d7a19a1f, received 84K ETC from 0x63a8ab05ae4a3bed92580e05e7dce3b268b54a7f in 5 transactions at 30–31 July, 2020
In total, before the attack, the total ETC value on these addresses was ~ 807K ETC ($5.6 million).
Transactions in non-reorged chain
When the attack started, nobody knew about it, as the attacker did not publish any blocks. However, the attacker created private transactions that we recorded in our second dataset ( non-reorged chain ).
This graph expands for the addresses that we mentioned before, shows how the attacker withdrew money from the Exchange to his/her own wallet and sent back the money to Exchange again.
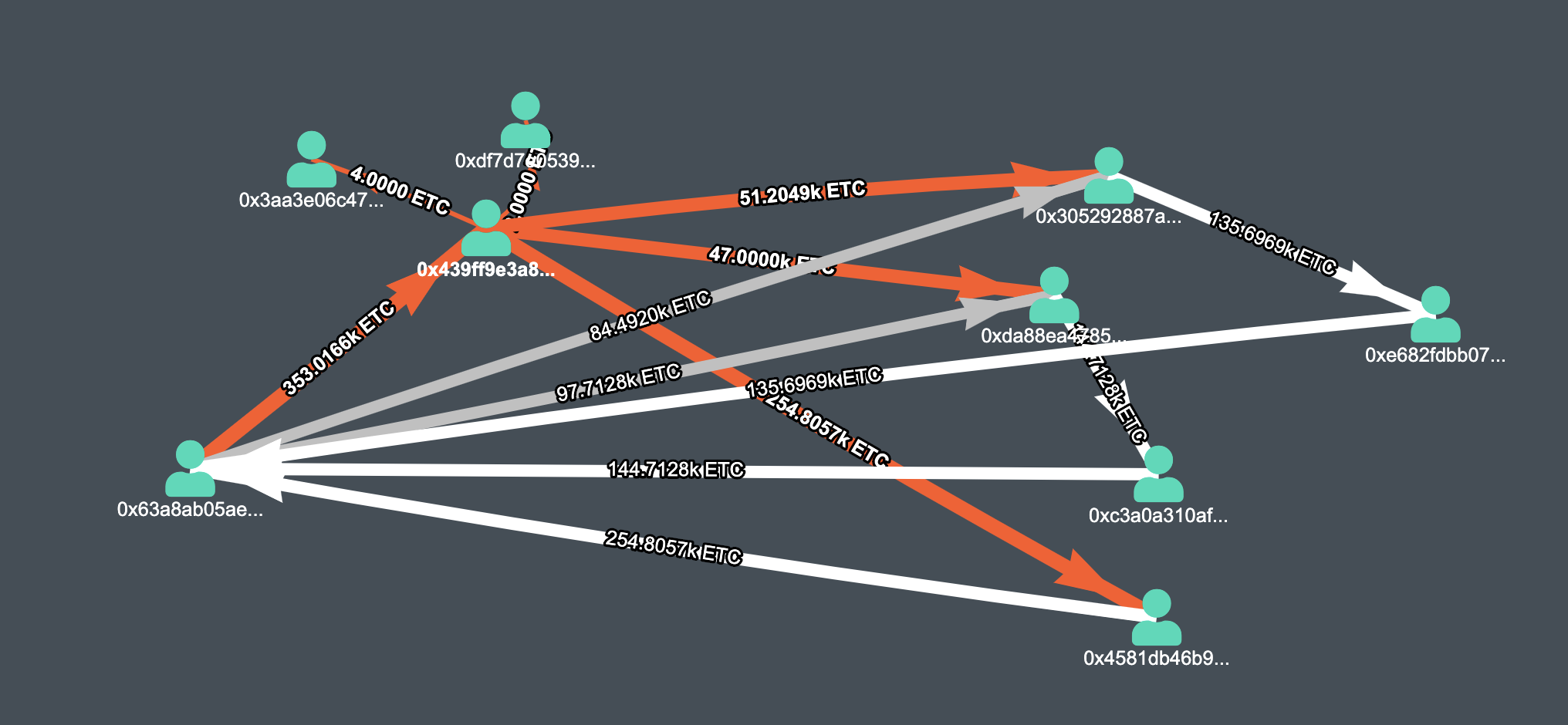
Graph of transfers made by the attacker, Note, that you have to manually expand addresses by double-click to get this picture.
When combining the data from Non-reorged chain and reorged chain, we can see that in the non-reorged chain, the money goes back to the Exchange:
- Before the attack, money was withdrawn from address 0x63a8 to the 5 different addresses. We believe 0x63a8 is an Exchange wallet.
- during the attack, the money was sent back to exchange 0x63a8 through 1–3 intermediary addresses
- As a result, all money withdrawn from exchange 0x63a8, got back to the exchange 0x63a8 and these transactions were confirmed as no one knew about the attack that was undergoing.
For example, the transactions below shows how the attacker sent money back to exchange in small portions:
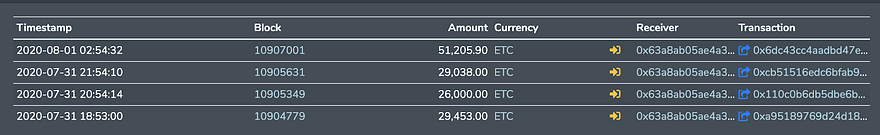
Money transferred by the attacker back to the Exchange
This was visible in the non-reorged chain, and these transactions were valid for at least 12 hours, while miner created new blocks privately.
As a result, the attacker got away with 807K ETC plus mining rewards ( 13K ETC ) by successfully executing the 51% attack on Ethereum classic. In total, it is approx. $5,650,820. Much more than money spent on mining ( $192K ).
Following attacker’s double-spent ETC
The attacker now needs to monetize the double-spent ETC remaining at his/her wallets. And here, we see a typical pattern of splitting amounts for many addresses and multiple hops transfers.
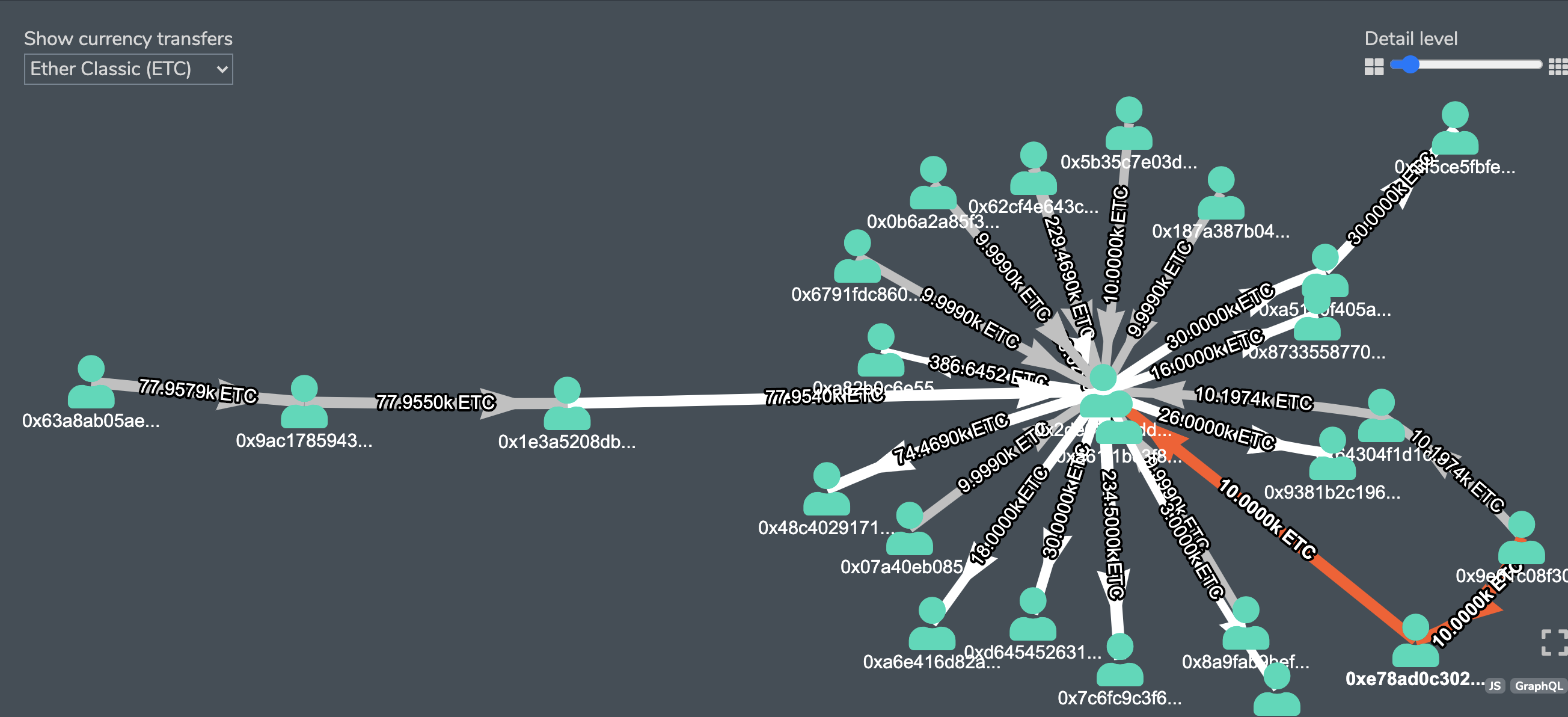
https://explorer.bitquery.io/ethclassic/address/0x1e3a5208db53be56b6340f732ec526b4bdc37981/graph, expanded to the right
However, with our Coinpath® technology, we traced the double-spent ETCs. The current distribution to the time of writing is:
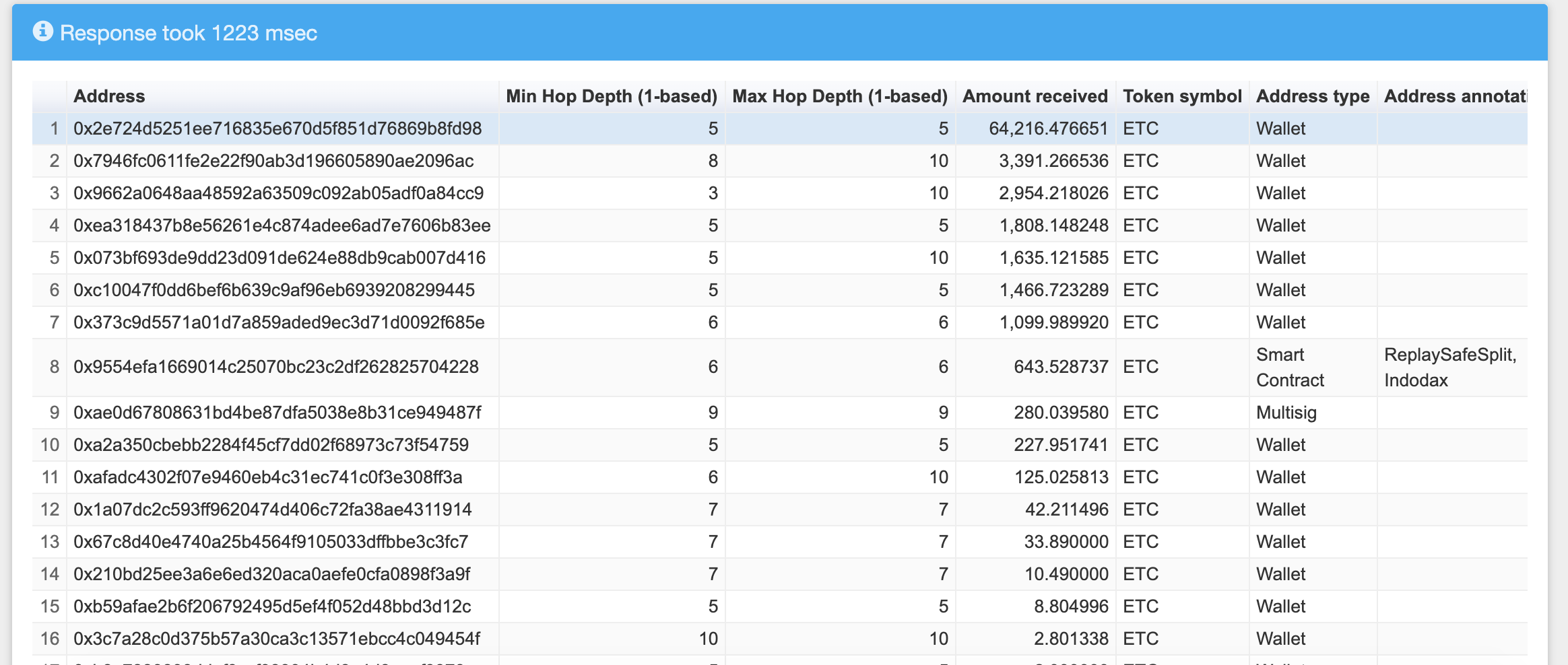
Coinpath API report starting from 0x1e3a5208db53be56b6340f732ec526b4bdc37981 address
Identifying the Crypto Exchange
We do not know the exact owner for the address 0x63a8ab05ae4a3bed92580e05e7dce3b268b54a7f, but we are pretty confident this is a Crypto exchange because of the high volumes in transactions and other behavioral patterns.
What we can guess is this address belongs to the OKEx exchange or its affiliates. The same address in Ethereum Mainnet has a lot of related activity to OKEx wallets.
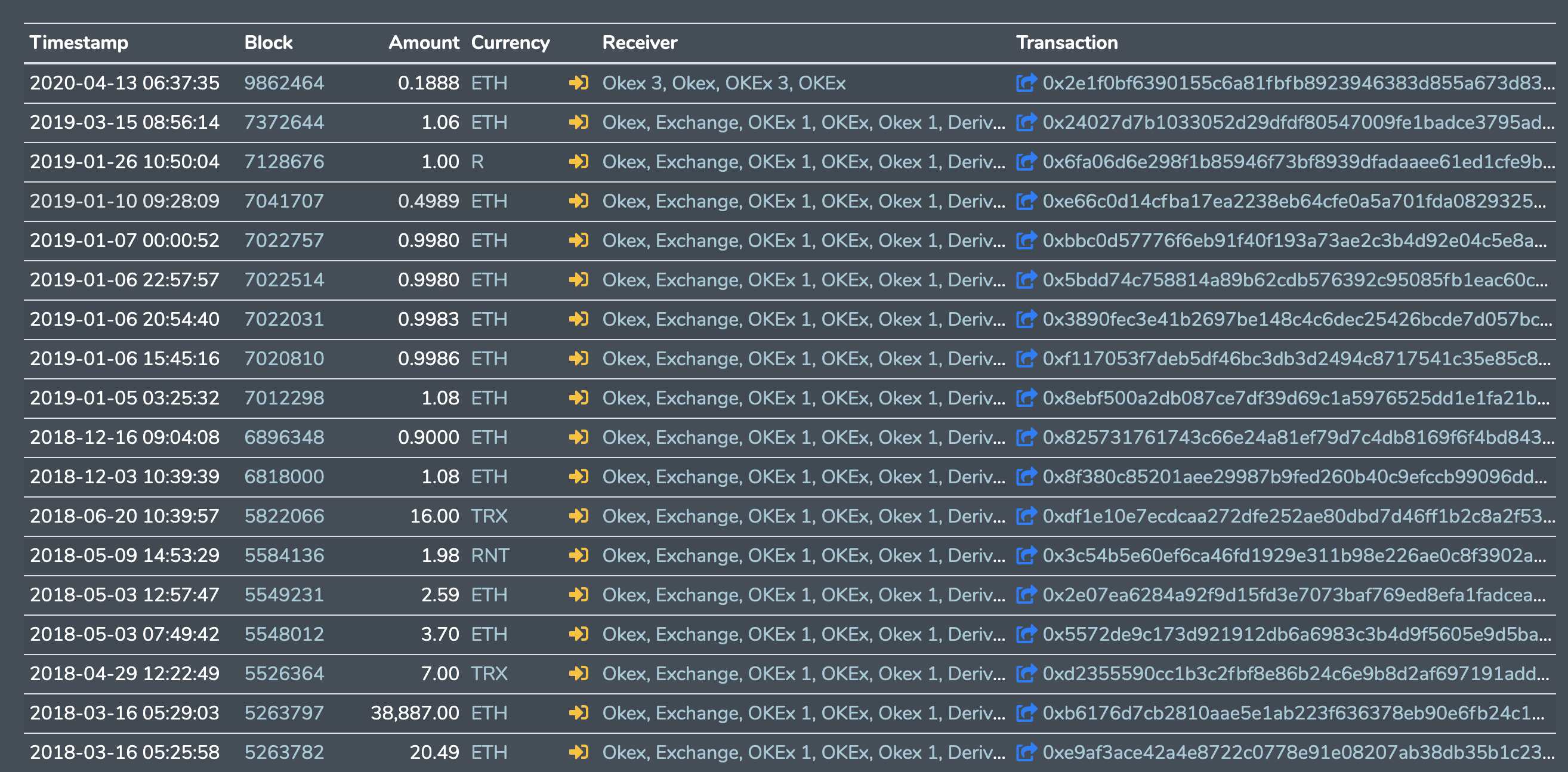
All transfers were with OKEx other wallets, https://explorer.bitquery.io/ethereum/address/0x63a8ab05ae4a3bed92580e05e7dce3b268b54a7f/outflow
Victor Fang, CEO of Blockchain Ecosystem Intelligence Anchain.ai, confirmed that this address belongs to the OKEx exchange.
Note: Special thanks to Victor Fang(Anchain) and Yaz Khoury for helping in preparing the article.
Also Read
- How Upbit hackers laundered millions using crypto exchanges?
- Cryptocurrency Money Laundering Explained
- Coinpath® – Blockchain Money Flow APIs
- Create a WhaleAlert like service in 10 minutes (Crypto Alert)
- Crypto chart widgets for your website (Including WordPress)
- Twitter Hack — Track Bitcoin crimes in real-time using Coinpath®
About Bitquery
Bitquery is a set of software tools that parse, index, access, search, and use information across blockchain networks in a unified way. Our products are:
-
Coinpath® APIs provide blockchain money flow analysis for more than 24 blockchains. With Coinpath’s APIs, you can monitor blockchain transactions, investigate crypto crimes such as bitcoin money laundering, and create crypto forensics tools. Read this to get started with Coinpath®.
-
Digital Assets API provides index information related to all major cryptocurrencies, coins, and tokens.
-
DEX API provides real-time deposits and transactions, trades, and other related data on different DEX protocols like Uniswap, Kyber Network, Airswap, Matching Network, etc.
If you have any questions about our products, ask them on our Telegram channel. Also, subscribe to our newsletter below, we will keep you updated with the latest in the cryptocurrency world.
Subscribe to our newsletter
Subscribe and never miss any updates related to our APIs, new developments & latest news etc. Our newsletter is sent once a week on Monday.


